Microsoft is looking to employ a new approach to keep malware risks at bay, courtesy of Project Freta. In short, Project Freta is Microsoft’s answer to malware threats that often go undetected and cause great trouble to individuals and companies, and gain enormous economic value. Malware that goes undetected is subject to reusability. Such malware threats always pose a great risk of recurrence. Microsoft’s new Project Freta initiative is likely to help prevent the recurrence of malware threats to a significant extent.
Microsoft launches Project Freta
Justifying the emergence of Project Freta, this is what Microsoft had to say in its recent blog post:
“Undetected malware can be continuously re-used: it is never part of attack reporting, never summons incident responders, and never alerts the victim to a data theft event. The economics of reuse can justify enormous attacker investment in malware non-discoverability. Conversely, once a malware strain is discovered, its value plummets in tandem with its reusability.”
What is Project Freta
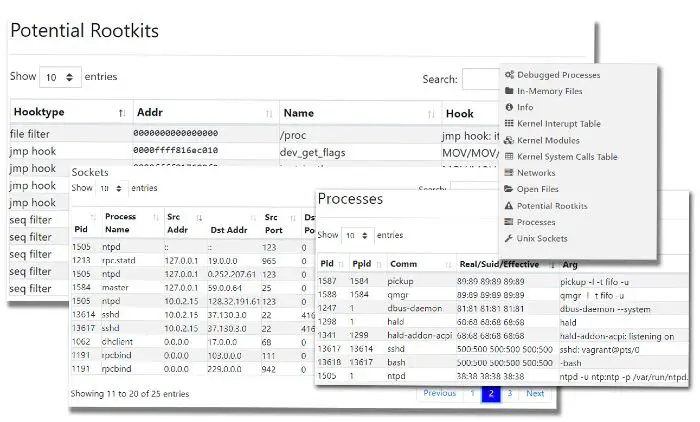
What is Project Freta, you ask? Project Freta is a cloud-based security service from Microsoft Research that enables automated full-system volatile memory inspection of Linux systems. Project Freta can:
- Perform cyber forensics and detect Rootkit malware, stealthy malware methods such as process hiding on Linux systems.
- Enable the submission of a captured VM snapshots to generate a report of its content.
- Perform memory inspect and detect malware without alerting malware threat actors.
- Automate IR-like discovery tasks directly into a cloud fabric.
Getting started with Project Freta
Project Freta is freely and publicly accessible without any cap on its usage. Before getting started with Project Freta, you need to authenticate with a Microsoft Account (MSA) or Azure Active Directory (AAD) account. Once started, you can obtain and submit a memory image for analysis and get results by using either user portal or API.
If you want to access the Freta portal, go to freta.azurewebsites.net.
Leave a Reply