If a report from Cyber Ark Labs is to be believed, a vulnerability in Windows could allow a malicious file to pass through Windows Defender. The anti-malware component of Microsoft Windows can be tricked by a technique, dubbed ‘Illusion Gap’ to scan a different file than the one designed for executing the malicious code.
Microsoft downplays ‘Illusion Gap’ technique alarm
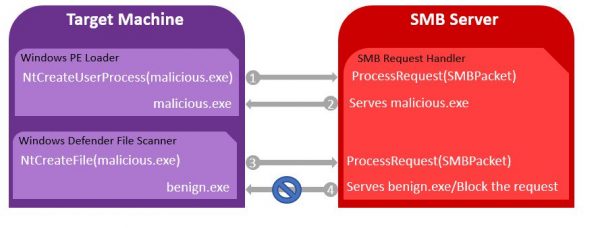
Illusion Gap relies on a mixture of both social engineering and the use of a compromised SMB server. Its infection is spread by the attacker by convincing a user to execute a file in a malicious SMB server under their control. When it is done, Windows requests for two copies of the executable; first to launch the program, and second for Windows Defender, which it scans for malicious content.
Since SMB servers can distinguish between the two requests, attackers can take advantage of this and configure it to send two completely different files. For example, the attacker can send a malicious file to the Windows PE Loader, and a benign file to Windows Defender marked as clean. So, when Windows Defender scans the clean file and gives the permission to go ahead, Windows PE Loader can execute the malicious file without Windows Defender realizing they’re two different things.
This appears to be a worrisome situation as more instances of this type could lead to more exploits in the future. When notified about this issue, Microsoft refused to acknowledge the problem as a security issue-
Thanks for your email. Based on your report, the successful attack requires a user to run/trust content from an untrusted SMB share backed by a custom server that can change its behavior depending on the access pattern. This doesn’t seem to be a security issue but a feature request which I have forwarded to the engineering group. Thanks again for reporting security issues to Microsoft responsibly and we appreciate your effort in doing so.
For more, you may visit the source.
Leave a Reply