A few months ago, computer systems worldwide were detected vulnerable to attacks named Meltdown and Spectre. All the companies like Microsoft and Intel issued patches for their devices and fix this vulnerability. Maybe because of this rush, Microsoft issued a patch that fixed the Meltdown flaw but in return gave rise to another flaw.
Ulf Frisk is a security researcher who pointed out that this Meltdown fix that was issued for Windows 7 only made the machine vulnerable to another flaw. Now, attackers would be able to gain memory read and write rights at higher speeds and eventually taking over the main control over the whole machine.
Patch to fix vulnerability caused by earlier patch released
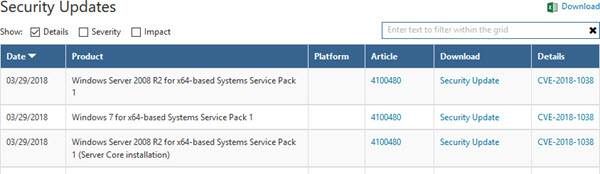
Microsoft documented this vulnerability in CVE-2018-1038 and rated it as severe on the basis of its capabilities. Microsoft says that no attacks have been detected as of now but as a patch to fix that is issued too, users are highly recommended to install that as soon as possible.
Microsoft said that
“An elevation of privilege vulnerability exists when the Windows kernel fails to properly handle objects in memory. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode.”
It is worth noting that Windows 10 is already immune to this flaw. And users running up to date version of Windows 10 need not worry much about this. But if you are running Windows 7 or Windows Server 2008 R2 on whatever machine and due to whatever reason, you need to fix this but installing the patch.
If you wish to manually get the installation file and get your PC safe, you can download it for your Windows 7 or Windows Server 2008 R2 machine by downloading it from the official Microsoft Catalog here.
If you are running Windows 7 for x64-based Systems or Windows Server 2008 R2 for x64-based Systems, and you have installed any of the servicing updates released during or after January 2018, you need to install 4100480 immediately to be protected from this vulnerability.
Leave a Reply