Chances are you have not heard of the GIFShell attack that was done through Microsoft Teams. From what we have gathered, hackers exploited legitimate configurations and features that haven’t been set correctly. We hope that security teams from within the many organizations around the world take note of this attack ad hardened configurations in their SaaS-based apps.

What is GIFShell attack method?
The GIFShell attack is a technique designed to give hackers the ability to take advantage of features found in Microsoft Teams. It acts as a C&C malware that steals data by the use of GIFs without being found by all types of monitoring tools. This attack method needs a user or a device that is already compromised in more ways than one.
The attack works by compromising a computer in a bid to add the malware. In a situation like this, hackers must convince users to install malicious malware on their devices. Now, the next step is for the hacker to create their own Microsoft Teams account, and from there, make contact with other Teams users that are outside of the organization.
From there, the hacker will work to get the specially crafted GIF into Microsoft Teams logs. When the stager finds this special GIF, it will extract and run the commands found inside of it says BleepingComputer.
What does Microsoft have to say about this problem?
For this case, 72412, while this is great research and the engineering team will endeavor to improve these areas over time, these all are post exploitation and rely on a target already being compromised. No security boundary appears to be bypassed. The product team will review the issue for potential future design changes, but this would not be tracked by the security team.
How to protect yourself against GIFShell attacks?
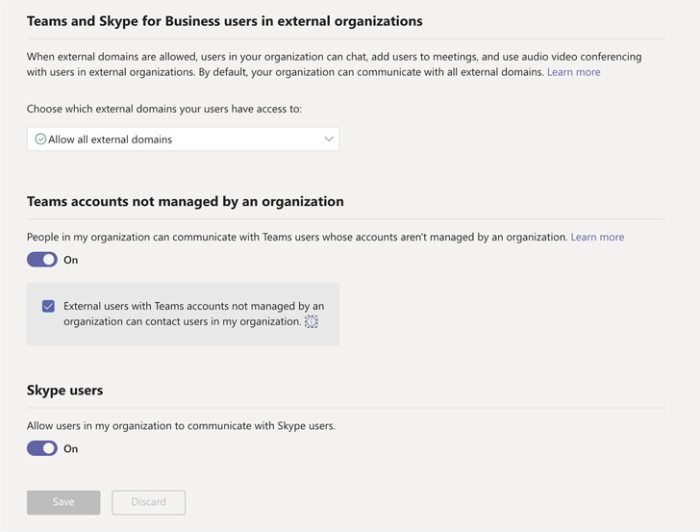
The first thing users should do is Disable External Access. This feature is turned on by default in Microsoft Teams but can be disabled with ease.
Most organizations have no idea they are allowing External Teams collaboration, and most have no use for it in the first place.
Leave a Reply