Microsoft has been distributing .NET Core Update as a standalone package or Runtime Updates until now. Starting December 2020, the .NET Core updates on Windows via Microsoft Update. This change comes from multiple requests made to Microsoft by Organizations and will allow them to manage the updates like the rest of the Updates.
However, in the Self-Contained Deployment model, apps are still responsible for keeping the runtime updated. One of the major features of delivering updates through this is that apps can automatically use the latest runtime versions once an update is deployed.
.NET Core Updates to be rolled via Microsoft Update
Microsoft will treat the .Net Core as an independent product, unlike the Framework, which is a component of Windows OS. Hence updates to .NET Core will always be distinct from .NET Framework and available on Microsoft Update (MU) and not Windows Update (WU).
It will ensure that a computer does not have multiple versions of the Framework installed but only the latest version.
However, it is still possible to block the .Net Core Update delivery from Microsoft Update by following this guide.
When you choose Microsoft Update aka MU, both security and non-security fixes for all supported versions of .NET Core (currently .NET Core 2.1, .NET Core 3.1, and .NET 5.0) will be available on MU. It includes .NET Core SDK, .NET Core Runtime, ASP.NET Core Runtime, and the .NET Core Desktop Runtime installers.
Once the update is installed, a reboot is required to uninstall the previous version. Pos that, it will restart IIS services.
How to enable .NET Core Updates via MU?
There are two distinctions here—Consume and IT. While Windows Consumers can install it by going to Settings > Update & Security > Windows Update > Advanced options and turn on Receive updates for other Microsoft products when you update Windows, IT admins need to setup Windows Server Update Services (WSUS).
How can IT Admin manage .NET Core Updates using WSUS?
Since IT admins need to configure multiple computers and selectively install the updates, WSUS makes more sense to distribute the update instead of connecting to the internet.
Under Products, they will need to select the framework under Developer Tools, Runtimes, and Redistributables. Under Classifications, they can select the following payload Security Updates, Critical Updates, or Updates—more on this on Microsoft Documents.
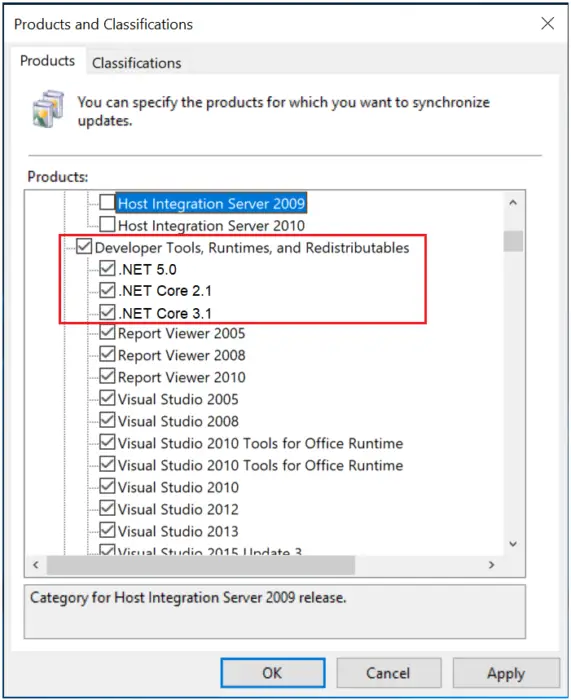
There is more. First Updates need to be synchronized with either Microsoft Update or an upstream WSUS server. Second, updates need to be approved before they are deployed on connected computers. This can be manual or automatic based on rules.
How to deploy updates using System Center Config Manager/Endpoint Config Manager
SCCM or MECM offers additional flexibility compared to WSUS. Microsoft recommends reading more about it on the official documentation.
How to Block .NET Core update delivery from Microsoft Update
Most users we asked told us they want their computers to be kept up to date and secure automatically for them, but we realize some customers may not want this. If you prefer not to have your .NET Core installation automatically updated, there are a few different options.
For computers that get updates from WSUS or SCCM
The first thing is to unapproved the Product entries and then deploy the following registry keys across the computers.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET\] "BlockMU"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET\5.0] "BlockMU"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET\3.1] "BlockMU"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NET\2.1] "BlockMU"=dword:00000001
The alternate way is to use the Group Policy to deploy the registry key to many computers at once.
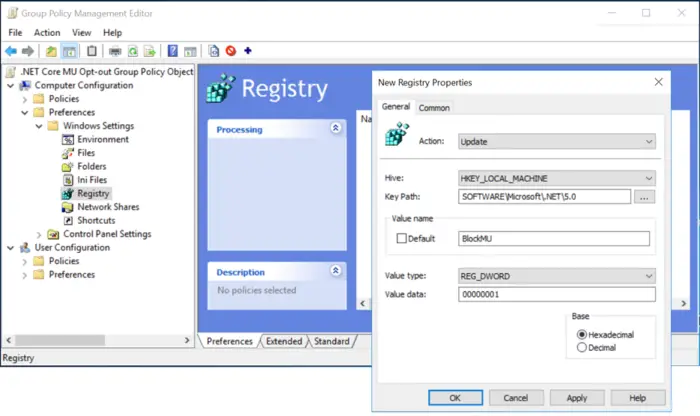
For computers that directly connect to MU for updates
End-users not connected to WSUS or anything can use the official registry keys offered by Microsoft.
- Block all .NET Core updates delivered by MU
- Block .NET Core 3.1 updates delivered by MU
- Block .NET Core 2.1 updates delivered by MU
Read more about it on the Official Microsoft news.
Leave a Reply