Cybersecurity researchers have discovered a new technique employed by the Metamorfo malware campaign that primarily targets financial firms. Banking trojans aren’t new phenomena. In the past, we have seen instances where hackers targeted sensitive information and tricked users into installing Trickbot malware, which ultimately served as a dropper for other malware threats.
Metamorfo uses DLL Hijacking
Initially discovered in April 2018, Metamorfo became subject to widespread media attention earlier this year. In a nutshell, Metamorfo is a financial malware known for targeting Brazilian companies in its initial days. But over the last few months, Metamorfo has added new capabilities while the malware has expanded its reach to several new regions and countries.
Cybersecurity firm Bitdefender has discovered one such technique where Metamorfo operators use trustworthy software components to compromise computers using DLL Hijacking.
“Metamorfo currently uses an extremely effective technique called DLL hijacking to conceal its presence on the system and elevate its privileges on the target computer. We also noticed that the malware tries to download other files from the C2 server, suggesting that it could download an updated version of itself with an extended command set as well.”
What is DLL Hijacking?
Before we get into DLL Hijacking, first, we need to understand what is DLL. As we have explained in the past, DLL stands for Dynamic Link Libraries. They are external components of applications that run on Windows or any other operating system.
In short, DLL files essentially store codes for other applications. They are loaded into RAM only when required, thus serving as extensions to different applications and saving memory.
DLL Hijacking invokes third-party code by swapping a code library with a malicious one or dropping a malicious library on the search path. Meaning, if an attacker finds a way to get a malicious file onto a victim’s computer, that file could be executed when the user runs a legitimate software application, which is vulnerable to DLL Hijacking.
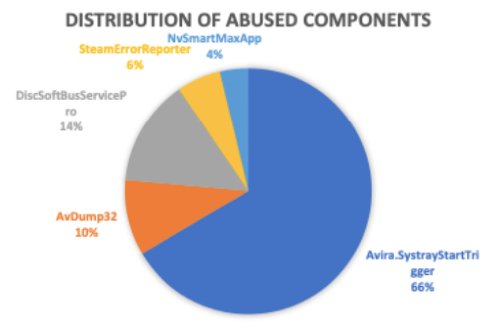
In such attacks, attackers generally use legitimate but vulnerable software applications in a way that it would naturally invoke a malicious DLL file. Researchers also discovered that attackers primarily target and abuse software components manufactured by Avira, AVG and Avast, Damon Tools, Steam and NVIDIA.
“Some components in these products load DLL files without ensuring that the files loaded are legitimate. This way, the malicious code is loaded and executed by a trustworthy process, so users will suspect nothing if they ever bring up Task Manager.”
Researchers also say some security solutions fail to detect malicious code at the firewall level.
Legitimate software applications are authenticated using the Code signing mechanism. The research raises serious concerns about the reliability of certain antivirus solutions since most PC users are likely to trust these applications when it comes to making changes to the system.
DLL hijacking using Metamorfo also poses security risks and challenges at organizations that allow digitally signed applications to run undisturbed.
Leave a Reply