Cybersecurity researchers have unearthed a new phishing campaign that pretends to be simple rather harmless. In this attack, hackers abused an Adobe campaign redirection mechanism to send victims to an Office 365 themed phishing website, courtesy of a Samsung domain.
Office 365 phishing campaign unearthed
According to researchers, the adoption of Office 365 in the enterprise community has exponentially increased over the last few years. The popularity of Office 365 has essentially drawn the attention of attackers whose primary motive behind launching such phishing campaigns is to steal Office 365 credentials.
“As 90% of cyber-attacks start with a phishing campaign, Office 365 is an attractive target for threat actors who work to evade the continuously introduced security solutions,” said Check Point Research.
Researchers have discovered what they describe as a “seemingly unsophisticated Office 365 phishing campaign.” In this attack, hackers exploited the redirection mechanism of Adobe Campaign, a series of solutions that help customers deliver personalized campaigns across all of their online and offline channels.
Attackers further used a reputable domain, case in point, Samsung. This way, attackers successfully dodged the bullet and bypassed security software, further redirecting potential victims to an Office 365 themed phishing website where innocent Office 365 users would end up revealing their login credentials to attackers.
Aiming to expand the scope of their phishing campaign, attackers further went to compromise other reputable websites to inject a malicious script emulating a similar redirect mechanism as the one from Adobe. Hackers also played several other tricks to “hide the phishing kit and avoid detection at each stage of the attack.”
“Neither Adobe nor Samsung were compromised in the sense of exploiting a vulnerability. Samsung’s Adobe Campaign server was left available for managing campaigns that were not necessarily part of the company’s marketing efforts.”
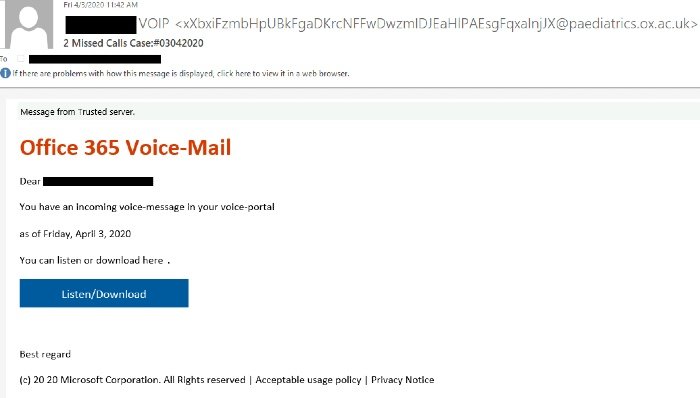
Check Point Researchers detected a phishing campaign that sent “missed voice message” emails to its victims. Interestingly, 43 percent of these attacks targeted European companies while the rest of the attackers targeted companies Asia and the Middle East.
The fake email alerts prompted users to click on a button that would them to their Office 365 account. What’s more, these emails also carried the “Message from Trusted server” notification at the top which is scary.
As soon as victims clicked the button, they were redirected to a phishing website pretending to be Office 365 login page. Interestingly, most of these emails came from multiple generated addresses referring to legitimate subdomains from the University of Oxford (UK).
“Using legitimate Oxford SMTP servers allowed the attackers to pass the reputation check for the sender domain. In addition, there was no need to compromise actual email accounts to send phishing emails because they could generate as many email addresses as they wanted.”
Here’s what made this campaign interesting
As researchers conclude, attackers used multiple tricks to avoid security hurdles at each stage. For example, hackers used an Oxford email server to send spam. It allowed them to circumvent the sender reputation filters and utilize generated email accounts instead of actual accounts.
Again, URLs mentioned within the email point to a high reputation domain owned by Samsung. Ultimately, it all led users to an Office 365-themed phishing website.
Leave a Reply