DDoS is a commonly seen attack on important websites and web portals. Today’s technological advents have successfully mitigated DDoS or Distributed Denial of Service attacks. However, the DDoS authors are now using unique and unrecognizable techniques for the attacks. A recent blog on Sucuri Blogs mentions a recent case where large CCTV botnet was used in the DDoS attacks. This is certainly a new type of weapon used in DDoS attacks, as the attackers were using only IoT (Internet of Things) CCTV devices as the source of their attack botnet.
How the usage of a CCTV botnet for DDoS attacks surfaced
Sucuri’s team found the usage of CCTV botnet for DDoS attacks through a simple requirement. This particular client of Sucuri had signed up with them to protect their site from a DDoS that had taken them down for days. It was a well-known later 7 attack that was generating 35,000 HTTP requests per second (RPS) which was more than their web servers could handle. Sucuri’s team was able to mitigate the attack and DDoS attacks stopped. However, as soon as the client’s site was up and running again, the attacks increased up to 50,000 HTTP requests per second. Surprisingly, unlike the typical DDoS attacks, these attacks have continued for days.
This is where Sucuri’s team dived in more and found that attackers were leveraging only IoT (Internet of Things) CCTV botnet for the DDoS attacks.
How CCTV botnet are used for DDoS attacks
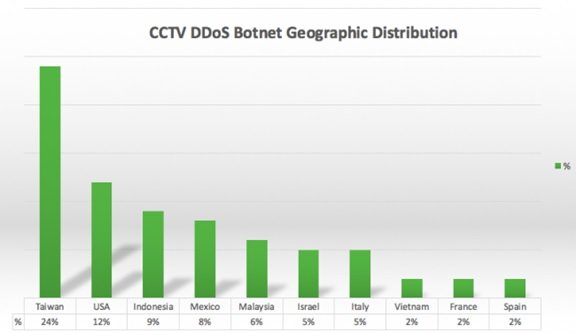
Usage of IoT devices such as CCTV botnet for DDoS attacks is also not new. However, the surprise lies in using the CCTV botnet for such a long period. Besides, the attacks were planned in such a way that the geographic location of the source won’t be found. This particular attack that used CCTV botnet generated 25,513 unique IP addresses within a couple of hours, which came from different countries and networks. However, most of the IP addresses belonged to Taiwan (24%), followed by USA (12%).
Stopping these kinds of huge DDoS attacks that use CCTV botnet is quite difficult. However, Sucuri’s team advises users that
“If you are an online camera user or vendor, please make sure it is fully patched and isolated from the internet. Actually, not just your online camera, but any device that has Internet access (from DNS resolvers, to NTP servers, and so on).”
The attacks are large. More than 25,000 CCTV devices have been compromised and used for the attacks as the CCTV botnet.
The Sucuri team learned that all of them were running the “Cross Web Server” and had a similar default HTTP page with the “DVR Components” title.
Leave a Reply