Malware embedded within malicious links are very common. In such malware, the user is prompted to click the link for the malware to do its job. But, researchers at Trend Micro have recently exposed a malware which only needs you to hover your mouse over a link for the malware to install itself. Introducing you to the new Malicious Mouseover Banking Trojan!
Malicious Mouseover Banking Trojan
According to researchers at Trend Micro, this Banking Trojan is a new type of malware which automatically steals a victim’s credentials and banking information when inside the user’s system.
The researchers examined the Trojan and found that it belongs to the OTLARD variant, which is also known as Gootkit. This Trojan has been in existence in the Internet world since 2012 and has grown into being a Trojan capable of remote access, network traffic monitoring, and other similar tactics.
This Banking Trojan has the power to steal bank information, it has attacked a campaign that involved France. The committers sent out files which seemingly looked like letters from the French Ministry of Justice.
How does it work?
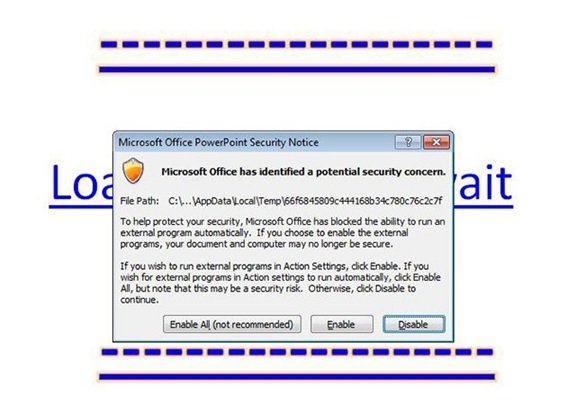
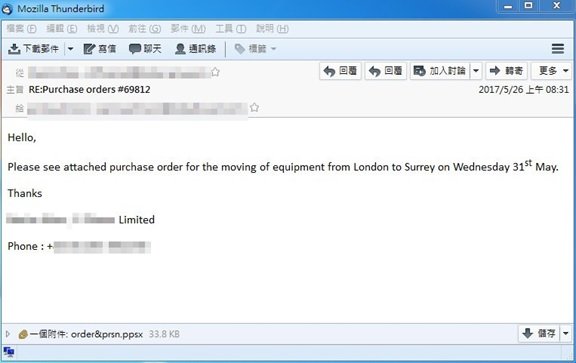
This new attack works in a very simple way. It takes advantage of a PowerPoint action which takes place when a user hovers over a link. The malicious link can be embedded in an image or in the text of a PowerPoint presentation. The victim downloads the PowerPoint file, the file opens inevitably into presentation mode, and the computer is infected as soon as one hovers over the malicious link. The email contains other files such as an invoice and a purchase order along with the PowerPoint file, PPS or PPSX.
Beware of TROJ_POWHOV.A and P2KM_POWHOV.A, this is the title of the malware.
Who is this Banking Trojan targeting?
The emails are targeted at companies involved in specific industries in Europe, the Middle East, and Africa. Targeted industries include manufacturing, education, logistics, and pyrotechnics.
The technique of a mouse-hover may work successfully in corporate environments where Office files are regularly sent and received with employees paying little consideration to what the file is.
According to Trend Micro,
“The trick will not work in Microsoft PowerPoint Online or Office 365’s “web mode”, as these don’t provide the actions functionality that is present in offline/desktop versions. An Office 365 end user, however, can still be affected if he accesses his account and opens the malicious file through a client (PowerPoint locally installed in the machine).”
User operating older versions of Microsoft Office at higher risks
According to the researchers, the user operating older versions of Microsoft Office are most likely to fall victim of banking trojan. The reason is, unlike the older version the latest version of Microsoft Office originally opens files in Protected View, hence preventing any malicious infections to get into the system.
Tip to prevent the attack
Update your Microsoft Office version and always use Protected View to read files. Another thing to note is, that since the attack uses the medium of email, increasing email security is another way to protect yourself against these types of malware attacks, says TrendMicro.
Leave a Reply