A malware attack or even an attempt is much like an aircraft crash, in both the investigators need to look for the clue on why it actually happened. Analogous to the black box in the aircraft, security researchers try to dig for something called Artefacts which are stored in logs, memories and also hard drives. Once again, time is of prime importance here, and if not acquired within the required time frame the entire exercise will be futile. Hard drives, on the other hand, tend to save the data for long and this has been a boon for forensics. However, lately the attackers are using the anti-forensic technique, that is leaving no trail.
Fileless Malware
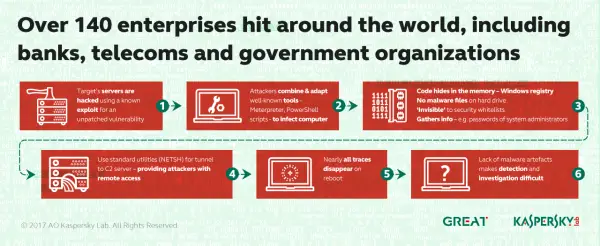
Duqu2 is an excellent example wherein the attackers simply drop the malicious package and then the malicious MSI package removes the package from the hard drive and renames itself. Furthermore, during the research, the Kaspersky team also found out that both malware and tunneling were implemented by attackers by making use of Windows standards including SC and NETSH.
The threat was initially detected by a bank’s security team and Kaspersky further names such kind of threats as MEM: Trojan.Win32.Cometer and MEM: Trojan.Win32.Metasploit.
Kaspersky Lab further participated in the forensic attack and discovered that it was carried out using PowerShell scripts within the Windows registry. Furthermore, it was also discovered that NETSH utility was used for tunneling traffic from the host to the attackers C2.
The script allocates memory, resolves WinAPIs and downloads the Meterpreter utility directly to the RAM. Thus its also called as Fileless malware. The scripts may be generated by using the Metaspoilt utility with some command line options. Once the script is generated successfully the attacker uses the SC utility to install a malicious service that is done by using another command line.
After this, in the next step, the fileless malware service will set up tunnels in order to access the infected machine from the remote hosts. The use of “SC” and “NETSH” will require administrator privilege and in order to make that happen the attacker will steal credentials from Service accounts.
On further investigation, it was discovered from the analysis of memory dumps and Windows registries from the machines that both the Meterpreter and Mimikatz were the tools used to collect passwords of system administrators. All of this resulted in the payload shown below. More than 140 enterprise networks have been infected with the PowerShell Scripts in the registry, reports Kaspersky.
Leave a Reply