Do NOT open any suspicious job application from your mailbox. It could be the Petya ransomware, discovered lately by security firm Trend Micro. Petya Ransomware is a new malicious program which overwrites the MBR (Master Boot Record) of your PC and leaves it unbootable, and also disallows restarting the PC in Safe Mode.
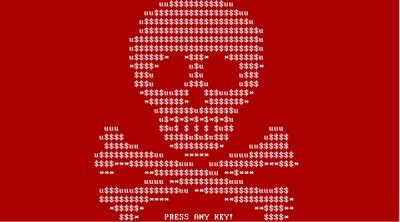
Petya Ransomware
Petya Ransomware reportedly is spread via emails, where the targets get an email masked as a job application. This malicious email contains a cloaked hyperlink to download applicant’s CV located at a specific Dropbox location.
This professed Dropbox folder contains a self-extracting executable file and a photo of the applicant. The so-called CV, which actually is a self-extracting executable file silently parks a Trojan on your system which further executes the Petya Ransomware. Like any other ransomware, this program also can easily blind any of your antivirus software.
Once installed, this program overwrites the Master Boot Record of your entire hard drive and causes a sudden Windows crash. This modified MBR doesn’t let the user reboot his PC and displays a red and white ASCII skull with a ransom message with a deadline saying,
“You became a victim of Petya Ransomware”
It demands a certain amount of bitcoins in exchange for the decryption key.
As per the report released by Trend Micro, the ransom price currently is $431 which is equal to 0.99 Bitcoins. Furthermore, the attackers warn saying that the ransom price would be doubled if the user misses the deadline shown on screen. The updated report, however, states that the malicious files hosted on Dropbox and its links are removed.
If you are seeing a flashing red and white skull and crossbones screen instead of your usual Windows icon, your PC is sadly infected with this nasty ransomware.
Download Petya ransomware decrypt tool & password generator
The PETYA ransomware is one of the most recent online threats for PC users. It is malware that overwrites the MBR (Master Boot Record) of your PC leaves it unbootable and also disallows restarting the PC in Safe Mode. Simply put, PETYA ransomware is malware that encrypts your PC and asks for a ransom against the decryption key.
While it is natural for users to panic in this situation and pay the ransom to get the decryption key, there is, fortunately, a decrypt tool available now. A new Petya password generator has been created to let the users decrypt their hard drives without paying any ransom. Yes! You can actually get your PETYA infected and encrypted disk back without paying a single bitcoin. However, the method is a bit technical and would not be easy for a non-techie PC user, it is still worth trying.
How to use Petya ransomware decrypt tool
To start with, you first need to extract some data from PETYA infected drive by connecting another computer to it. You need to get the 512 bytes of verification data and 8-byte nonce, to be precise. You can also use some hex editor to get the verification and nonce sector from the encrypted disk.
Data Location:
Nonce 8-bytes: sector 54 [0x36] offset: 33 [0x21]
Encrypted Verification Sector 512-bytes: sector 55 [0x37] offset: 0 [0x0]
- Save the files as src.txt and nonce.txt.
- Head over to Leostone’s decryption website petya-pay-no-ransom.herokuapp.com to use the genetic solver which gives you the decryption key in just a few seconds.
- This webpage has two fields where you have to paste the requested data from the infected drive.
- Click on ‘Submit’ and wait for a few seconds. The password generator will generate your decryption key.
- Go back to your encrypted disk and enter the generated decryption key when prompted.
- Your drive will be decrypted for free, without paying any ransom.
PETYA ransomware infects your computer and leaves no way to interact with the hard drive, but this online tool created by Leostone give you the access back in just a few seconds.
This is what the webpage title on Github says, “Get your Petya encrypted disk back, WITHOUT paying ransom!!!”.
Leave a Reply