PyLocky is relatively new ransomware written in Python, which is responsible for encrypting all the files on the victim’s computer and then ask for a ransom to let the user access their encrypted data by decrypting them. Till date, the victims either had to restore date from their backups or pay to get access if they did not have backups. Fortunately now, Talos has released a free PyLocky Decryptor Tool that can help victims decrypt their data.
Ransomware has been one of the most lucrative ways to earn revenue for cybercriminals. While domestic users may not worry much about their data held hostage, the organizations do have a lot to worry. Most of them prefer shelling out the ransom as it is far less than the damage the Ransomware would otherwise inflict. The implementation of Ransomware differs from one individual to the other.
PyLocky Decryptor Tool
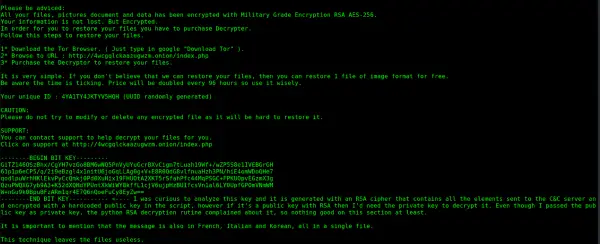
This tool requires the capturing of the initial PyLocky command and control (C2) traffic of an infected machine. It will only work properly on infected machines where the network traffic has been monitored. If the initial C2 traffic has not been captured, the decryption tool will not work.
The blog post states:
When PyLocky executes, it generates a random user ID and password and gathers information about the infected machine using WMI wrappers. It also generates a random initialization vector, or IV, which is then base64 encoded and sent to the C2 server along with the system information the malware has gathered. After obtaining the absolute path of every file on the system, the malware then calls the encryption algorithm, passing it the IV and password. Each file is first base64-encoded before it is encrypted. The malware appends the extension “.lockedfile” to each file it encrypts – for example, the file “picture.jpg” would become “picture.jpg.lockedfile.” The original file is then overwritten with the attacker’s ransom note.
PyLocky has targeted businesses in Europe and mostly in France and doubles the ransom amount every 96 hours – so this tool comes at the right time.
If you affected, you could get the latest version this file from GitHub.
TIP: There are more free Ransomware Decryption Tools here.
There are some basic steps one can take to prevent ransomware, including making use of some free anti-ransomware software. But should you have the misfortune of getting infected then this post will tell you what to do after a Ransomware attack on your Windows computer?
Leave a Reply