Ransomware has been creating havoc and is shaping up as a very convenient way for hackers to extract money. In fact, the dark web is filled with people who offer Ransomware as a service and eventually get a cut out of the extracted money. Ransomware is never the same they keep on manifesting in one form or the other so that the user is attacked unaware.
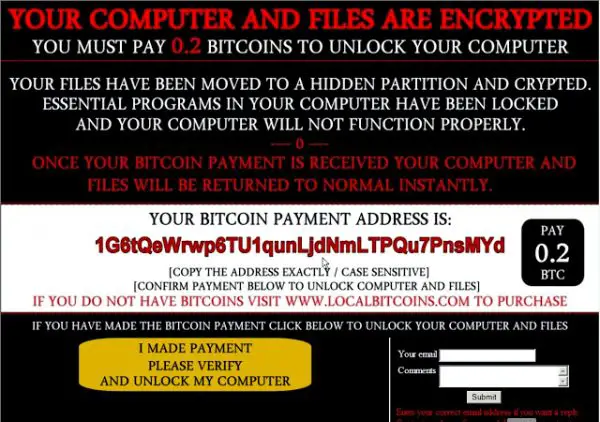
Ranscam Ransomware
Ranscam is one such new Ransomware that mostly piggybacks on the psychology of the people and uses a much simpler approach. While it is not always possible for the hostage to recover the files despite paying the ransom most of the times they do yield and pay up instead. This also reminds us to warn the users that they have an offline backup method in handy instead of relying on paying up the Ransom when infected.
Ranscam seems to be a brainchild of a clever thief who knows the worth of the victim’s data and the very fact that they would shell out Ransom to gain access to the same. While the attackers can always verify on whether they have received the hostage cannot confirm if the attacker will recover his file.
Modus Operandi
The attacker uses two jpeg banners to inform the user that they have been attacked along with a small box at the bottom that has a verify button. The author of the attack also displays his Bitcoin address and assures that once the payment is received the files will be decrypted. The program runs two HTTP GET requests to fetch the PNG images used in the verification process despite the fact that there is no actual verification happening.
The files have already been deleted and the Ranscam doesn’t have a built-in recovery system which means that even if you part with your entire fortune it’s most unlikely that the files will be returned. The Ransomware actually comes packaged in a .NET executable file signed using a digital certificate and issued to reca.net. Furthermore, the victim makes use of Task Scheduler to create a scheduled task that would run itself every time the machine is restarted and it also drops an executable into %TEMP%\.
The batch runs in several iterations and simply deletes the files and also tries to destroy the Windows by deleting the core Windows which is responsible for System Restores, Shadow copies and also the registry to disable the task manager. The attacker also seemed to be willing to give free tech support in order to increase the likelihood of a ransom pay-out. The Ranscam is one of the finest examples that threat carriers cannot be trusted and it’s always safe to have an offline backup of your important stuff.
Source: Cisco Telos Blog.
Leave a Reply