Ransomware is slowly gaining traction with antivirus manufacturers. The antivirus is trained especially to find strains of ransomware coming from unknown sources. But ransomware operators are trying to stay a step ahead by disguising the malware as installer packages used for mainstream software.
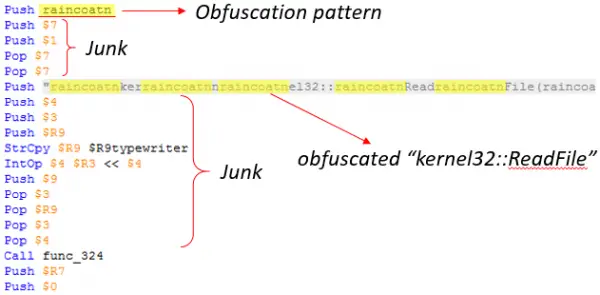
The Microsoft Malware Protection Center recently found out that a wave of new NSIS installers was being used in ransomware campaigns. These new installers pack significant updates, indicating a collective move by attackers to dodge AV detection by changing the way they package malicious code. These changes are observed in packages that drop ransomware like Cerber, Locky, and others.
An NSIS or Nullsoft Scriptable Install System is a system file that a lot of Ransomware operators use to sneak through firewalls. With antivirus striking down on these techniques, the operators are becoming even more careful by fitting in other non-malicious elements to make the package seem harmless.
The attackers use these types of tricks to pass through security filters.
- Non-malicious plugins, in addition to the installation engine system.dll
- A .bmp file that serves as a background image for the installer interface, to mimic legitimate ones
- A non-malicious uninstaller component uninst.exe
This recent trend of sending unique NSIS installers has seen a massive uptick since the operators discovered the AV vulnerability against them.
In older versions of malicious NSIS installers, the package contained a malicious DLL that decrypts and runs the encrypted data file, which contains both the encrypted payload and decryption code. What these newer versions are doing is that they eliminate the need for a DLL file in the first place. Instead, the entire installer is malicious and targets the system files in your computer.
NSIS ransomware is commonly found in the email versions of malware. Operators send these files discreetly in the form of email delivery notifications. The installers are usually in .zip or Javascript format that allows them to download the NSIS installer when accessed by the user. This NSIS then decrypts automatically and installs malware on the target files.
Microsoft recommends enabling Windows Defender Antivirus to detect these special installers. You can also use Windows Defender Advanced Threat Protection to alert security operations teams about suspicious activities.
Leave a Reply