According to a report published by Network security company, SonicWall, there was a decline in the Malware attacks in 2016, however at the same time Ransomware attacks multiplied by hundreds.
Statistics reveal that unique malware samples collected fell to 60 million as compared with 64 million in 2015, therefore a 6.25 percent decrease. There was a decline in Total attack attempts too, with the figures dropping for the first time to 7.87 billion from 8.19 billion in 2015.
SonicWall’s 2017 Annual Threat Report attributes the drop in Malware attacks to the following reasons:
- Point-of-sale (POS) malware attacks fell by 93 percent – The number of new POS malware variants decreased by 88 percent since 2015 and 93 percent since 2014. Recalling, the year 2014, the SonicWall GRID Threat Network observed an increase in the number of new POS malware countermeasures developed and deployed by 333 per cent. Owing to the better security measures like chip‐based POS systems coupled with better understanding of the vulnerabilities and risks associated with digital environments, the attacks reduced drastically.
- Secure Sockets Layer/Transport Layer Security encrypted traffic grew by 38 percent: SSL/TLS encryption jumped from 5.3 trillion web connections in 2015 to 7.3 trillion in 2016 partly due to the growing cloud application adoption rate. SonicWall detected 62% web connections following SSL/TLS ‐ encryption.
- Popular Malware families like Angler, Nuclear, and Neutrino died in 2016: In mid-2016 leading exploit kits like Angler, Nuclear, and Neutrino disappeared. While Angler died, post the arrest of 50 Russian hackers, Nuclear and Neutrino could only surge a bit before fading out in the latter half of 2016.
Ransomware sees a massive jump, steals $1 billion from victims
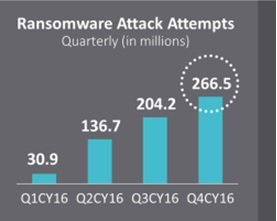
If you think that Security professionals were successful in curbing Malware attacks, then it was only because their authors were busy making Ransomware.
The meteoric rise of ransomware in 2016 is a cause for concern. The SonicWall Report detected an increase from 3.2 million ransomware attack attempts in 2014 and 3.8 million in 2015 to an astounding 638 million in 2016. Recording an increase of 167 times in 2016.
What worse is that by the end of the first quarter, $209 million in ransom was paid by the companies, and by mid‐2016, almost half of organizations reported being targeted by a ransomware attack in the prior 12 months.
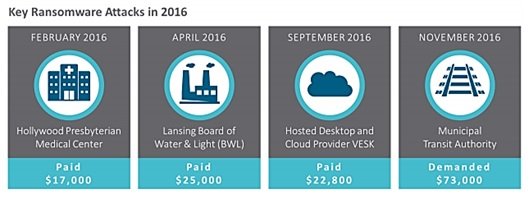
On high profile Ransomware cases of 2016, SonicWall report mentions,
Hollywood Presbyterian Medical Center in Los Angeles admitted to paying $17,000 in bitcoin to regain access to its data in February 2016, while the Lansing Board of Water & Light (BWL) revealed they paid ransomware attackers $25,000 in April 2016.x, xi In the U.K. in September 2016, hosted desktop and cloud provider VESK handed over 29 bitcoins, worth about $22,800 USD at the time.xii And in November 2016, the San Francisco Municipal Transit Authority had to open its fare gates when a ransomware attack took down its payment and email systems, demanding 100 bitcoins, or about $73,000 at the time.
Following were the key Ransomware trends of the year 2016,
- Locky was the most popular Ransomware spreading via malicious email campaigns
- All industries were attacked by ransomware authors
- Exploit kits began using ransomware as a payload
- Companies in the United Kingdom were 3x as likely as United States companies to be targeted by ransomware
Finally, the majority of successful Ransomware attacks were delivered via phishing emails. At times they were also hidden in encrypted traffic, defying even the walls of the SSL.
Other vital findings of the Ransomware attacks, can be read the report here.
Also read: What to do after a Ransomware attack on your Windows computer?
Very good and true article! And yes, most ransomware is nw.js and now skating right past even Edge, Chrome browsers (e.g., Serpent ransomware) via macros like photos, docs; Google itself may keep .js files from running in browser, but without good A/V or HIPS, any doc or pix could carry threat of some ransomware encrypting files upon opening. Cheers!