When it comes to cyber-attacks, Ransomware is the latest breed which is threatening both individuals and corporates. This particular breed of cyber-attack has made many millions of dollars from all across the world.
According to computer experts, the use of Ransomware has doubled in the last year. This time its knocking yet another new part of the world, which is China. Yet, the opening attacks into this particular market was made with several mistakes.
Chinese language Ransomware
There are some Chinese hackers who are launching sophisticated Ransomware attacks. In these attacks, these hackers hijack machines and demand payment to decrypt them.
TrendLabs reports that researchers have come across multiple samples of what appeared to be Chinese-language Ransomware. These samples were detected as Ransom_SHUJIN.A. and all of these samples could be opened into the same executable file.
Chinese Ransomware uses simplified Chinese characters for first time
This is not the first time when Chinese-language Ransomware has been found, but it may be the first time that hackers have used simplified Chinese characters. Such simplified Chinese characters are set to favor the use in mainland China. For this particular writing, the infection path of this attack is still unknown.
Here is what happens in Ransom_SHUJIN.A. Attack
- Similar Language Used
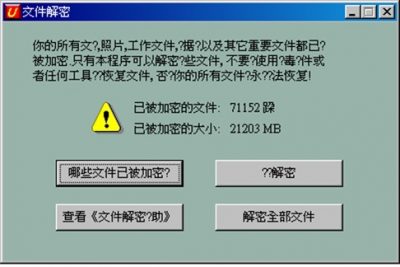
Initially you get a Warning message from Ransomware as follows:
Here the language is very much similar to those used in other Ransomware attacks. It states the below information to the user-
- The user’s files are getting encrypted
- The count of the total number of files encrypted
- The actual size of the encrypted files.
- Comparable Ransom Notes & Instructions
The note given here is very much comparable to the notes used in other Ransomware attacks. It gives clear instructions to download the Tor browser, which directs the user to connect to the attacker’s dark web site.
- Attackers are fluent in Chinese
With the kind of language used in the notes in seems that the author (attacker) is quite fluent in Chinese. The instructions given in the note have been modified to suit local conditions. The Author has recommended Baidu instead of Google, as a way to find the Tor browser. Further, the author has also mentioned the use of VPN or proxy to get around the blocks forced on the usage of Tor in China. Like other attacks, the instructions on this dark web site are also similar to each other. The URLs used has been marked in the above picture, these URLs lead to:
- hxxp://eqlc75eumpb77ced[.]onion/Decrypt.exe – updated copy of Ransom_SHUJIN.A
- hxxp://eqlc75eumpb77ced[.]onion/GetMKey.JPG – step-by-step instructions
- hxxp://eqlc75eumpb77ced[.]onion/btc/ – bitcoin tutorials
- hxxp://eqlc75eumpb77ced[.]onion/btc/help.html – bitcoin tutorials
- hxxp://eqlc75eumpb77ced[.]onion/DeFile.JPG – more instructions
Ransom_SHUJIN.A. – Ransomware attack OR Crypto-ransomware attack
Conversely, few things do not match with each other with the SHUJIN ransomware. This attack is called a Ransomware attack and not a crypto-ransomware attack. This is because of the fact that despite the language in the note, there was no encryption which actually took place.
Likewise, in this attack the usage of Bitcoin and Tor for ransom payments is quite infrequent. To use Tor and to acquire bitcoins requires some technical knowledge to carry out this method. In this case the attackers were reachable via a QQ number, while the popular local payment solution Alipay was neglected.
Since SHUJIN’s attack showed that the attackers weren’t too familiar with the Chinese Internet landscape, hence reports suggests that the attackers were located outside the country although the attackers have used good Chinese grammar suggesting that they may be from China itself. There is a strong possibility that future attackers will improve and further target Chinese users more effectively, which might allow them to pay in an easier and familiar manner.