Ransomware is one of the deadliest malware variants in recent history. While other malware may alter or edit your documents or settings, ransomware is a complex form of extortion. But ransomware cases seem to be going down month on month, despite that fact that it was the most popular malware in all of 2016.
Here are some insights from the Microsoft Malware Protection Department.
- Every quarter, more than 500 million emails sent by spam campaigns carry ransomware downloaders that attempt to install ransomware on computers
- These ransomware downloaders found their way into 13.4 million computers
- On the other hand, 4.5 million computers were exposed to the Meadgive and Neutrino exploit kits, whose primary payload is ransomware.
- The ransomware payload of these spam and exploit kit campaigns were observed in 3.9 million computers in 2016.
Ransomware is enabling hackers to get into any kind of public service system to extract money in return for the captured files. For instance, a California hospital had to forcefully pay up a ransomware attacker because he had hold of the hospital’s crucial patient files. Putting lives at risk, without a care in the world, makes this malware extremely fatal.
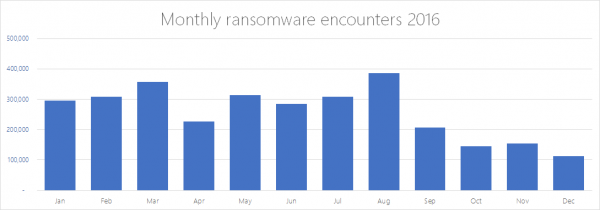
These reports from Windows Defender Antivirus show a rather unusual trend in the growth of ransomware last year. After peaking in August with a record 385,000 reports, incidents of the malware almost halved in September and the drop has since expanded.
TRENDS FROM ATTACK POINTS
Surprisingly enough, attacks points of ransomware didn’t so much distortion, as seen in the case of actual ransomware incidents in 2016.
There wasn’t a decline in the volume of emails that carry ransomware downloaders. In the last quarter of 2016 itself, more than 500 million such emails were sent. Clearly, this indicates that attackers haven’t given up on sending malware-filled emails to normal users. They have not stopped trying to infect computers with ransomware. In fact, up until the very end of 2016, there were multiple cases of Nemucod email campaigns delivering Locky and Donoff campaigns delivering Cerber.
Contrary to email ransomware, exploit kits seemed to have slowed down at the same time as ransomware attacks halved. There are two major exploit kits that help spread ransomware across networks, namely Neutrino that installs Locky, and Meadgive that installs Cerber virus. Apparently, Neutrino started scaling down in September as its operators reportedly went private, opting to cater to select cybercriminal groups. But Meadgive refused to stop, and analysts detected a Meadgive campaign was distributing the latest version of Cerber, primarily in Asia and in Europe, as late as December 2016.
INNOVATIONS IN THE FIELD
One of the biggest reasons of ransomware developing into the biggest menace is the kind of innovation that goes into the field. With its primary focus on multifold extortions, getting in brighter minds to work on newer techniques is easy in the ransomware industry.
- Server Targeting: With ransomware that specifically targeted servers, IT administrators not only need to protect endpoints, they also have to forcefully spend money to ramp up their server protection.
- Worm Capabilities: Attacks didn’t need to rely on campaigns to move from endpoint to endpoint. Ransomware identifies network drives, logical drives, and removable drives that it can use to spread.
- Alternate payment methods: Moving on from the traditional extortion method of taking Bitcoin, cybercriminals have since moved onto Telegram Messenger and Skype to extract money from other sources.
A GLOBAL THREAT
- United States: Cerber remained the most popular ransomware virus at 27% infection rate. Locky was a close second.
- Italy: Older versions like Critroni was most popular in the country. It is usually available in European languages.
- Spain: The country saw a variety of ransomware versions in equality, with Locky and Cerber also a part of the lot.
Read more about the insights on TechNet.
Leave a Reply