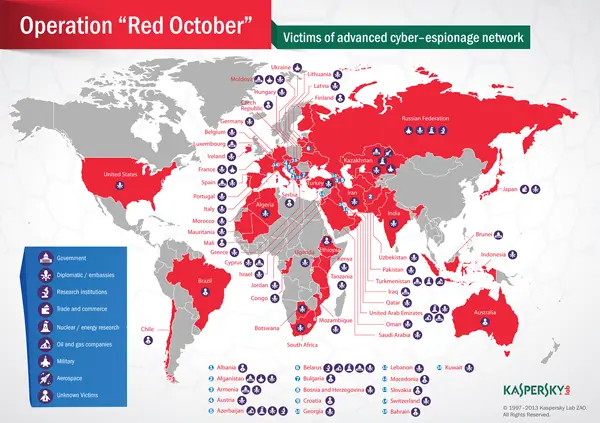
Kaspersky Lab’s research team has uncovered an advanced cyber spying network, dubbed ‘Red October’. It is supposedly targeting many governments, businesses, political groups, and other organizations, reports Kaspersky. The main purpose of the operation appears to be the gathering classified information and geopolitical intelligence of various nations.
The campaign attack is made up of spear-phishing, malware installation and exploits. The main malware first infects the system and later downloads modules used for lateral movement. For the first few days, the malware collects information about the system and identifies key systems in it. Only then, it deploys modules to compromise other computers in the network.
The discovery was made after an exhaustive five-year investigation carried out alongside numerous Cyber Emergency Response Teams (CERTS). As of now, Kaspersky hasn’t educated us much about kind of data may have been stolen over the five years while the complex virus was still active. Also, it hasn’t named the nations yet that it suspects to be involved in the plot, but confirms it has been a collaborative effort.
Kaspersky further describes the nature of the ‘Red October’ by saying the malware has a number of unique features that separates it from common infections. Among these, is ‘Resurrection module’ that permits the malware to hide itself in Microsoft Office and Adobe Reader programs after it has been detected. This offers it the ability to re-infect the machine again when it feels the time is favorable.
Besides regular PCs, the malware is also capable of affecting devices such as iPhones and Windows 8 smartphones. Majority of victims that have been affected by Red October are from Eastern Europe.
“The primary focus of this campaign targets countries in Eastern Europe, former USSR republics and countries in Central Asia, although victims can be found everywhere, including Western Europe and North America,” mentions report.
Get complete report from here.