Symantec has discovered a dangerous spying Trojan called as Regin that could have been involved in spying operations against government bodies internationally. What’s most shocking about this Trojan is the fact that it has operated for so many years without being marked. Regin is possessed with a superior technical competency that is rarely seen in other malware programs. It is a back door-type Trojan that could have been used to spy in government organizations, infrastructure operators, businesses, researchers, and private individuals to leak sensitive information.
Regin Trojan
This Spying Trojan has an exceptional multi-stage loading architecture! As Symantec describes, Regin exhibits exceptional capabilities and possess a multi-staged threat with each stage hidden and encrypted, with the exception of the first stage. Executing the first stage starts a domino chain of decryption and loading of each subsequent stage for a total of five stages. Each individual stage provides little information on the complete package. The threat can be analyzed only if all five stages and detected and intercepted.
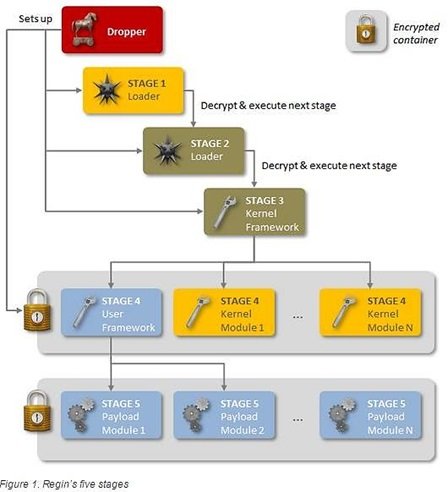
Regin could be transmitted by deceiving visitors to visit spoof version of well-known websites, through a web browser or even via a doctored application. On one computer, log files showed that Regin originated from Yahoo! Instant Messenger through an unconfirmed exploit, said Symantec.
Once installed, Reign can play a number of dirty tricks, like capturing screenshots, taking control of the mouse’s point-and-click functions, stealing passwords, monitoring network traffic, and recovering deleted files.
What makes Regin particularly dangerous is its ability to maintain a low profile and remain undetected. This quality ensures that the spying Trojan in able to run successful stealing campaigns for years.
Small businesses – Usual targets
As per Symantec’s report, Regin has particularly targeted private firms and small businesses which are comparatively easy targets compared to bigger organizations. Although the target includes private companies, government entities and research institutes, almost half of all infections targeted private individuals and small businesses.
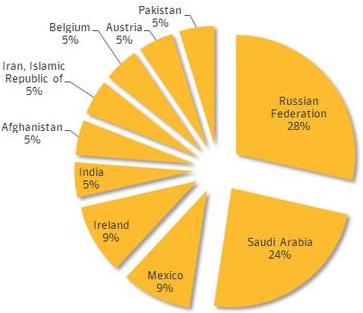
Hinting that targets may be region specific, attacks has been identified mainly in 10 different countries, with most concentration found in Russian federation. Surprisingly, the US did not feature in the target list published by Symantec.
Leave a Reply