A typical ransomware is a threat affects consumers and enterprise the same way. Basically, it’s a malware used as an exploit kit campaign, a payload to spam email, or a macro malware. It prevents the users to access their data or worse, login into their accounts and systems. In exchange for recovering the files from their encrypted form, a ransomware extracts money from the user. This is a typical strategy seen a ransomware. However, a newly detected ransomware called Samas uses a slightly different strategy to get into the system. Microsoft recently published a blog mentioning all necessary information about the Samas ransomware.
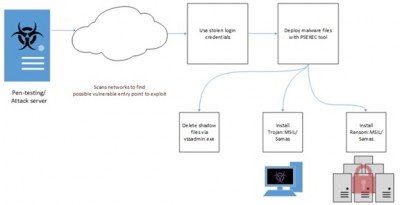
Strategy that Samas ransomware uses to infect the system
Saman ransomware or also known as MSIL started its malicious activities in the past quarter. According to Microsoft’s blog, this ransomware has a more targeted approach of getting installed than other malware. This threat requires other tools or components to aid its deployment. This is how Samas ransomware infection chain operates.
Microsoft states that,
“It starts with a pen-testing/attack server searching for potential vulnerable networks to exploit with the help of a publicly-available tool named reGeorg, which is used for tunnelling. Java-based vulnerabilities were also observed to have been utilized, such as direct use of unsafe JNI with outdated JBOSS server applications.”
According to Microsoft’s team, the Samas ransomware can use other information-stealing malware (Derusbi/Bladabindi) to gather login credentials as well. They further mention that when the malware has done so, it will list the stolen credentials into a text file, for example, list.txt, and use this to deploy the malware and its components through a third party tool named psexec.exe through batch files that are detected as Trojan: BAT/Samas. B and Trojan: BAT/Samas. C.
The team further adds that one of the batch files, Trojan:Bat/Samas.B also deletes the shadow files through the vssadmin.exe tool. Trojan:MSIL/Samas.A usually takes the name of delfiletype.exe or sqlsrvtmg1.exe and does the following:
- Look for certain file extensions that are related to backup files in the system.
- Make sure they are not being locked up by other processes, otherwise, the trojan terminates such processes.
- Delete the backup files.
Areas where Samas ransomware is detected
Majority of the Samas ransomware infections are detected in North America, and a few instances in Europe. However, some other regions in Asia such as India are also affected by this ransomware. Read more about Ransomware in India.
However, Microsoft also mentions that it is possible to prevent the infection. Microsoft suggests the use of Windows Defender for Windows 10 as your antimalware scanner, and ensure that MAPS has been enabled.
Read more information about Samas ransomware on TechNet blog.
Stay safe, prevent Ransomware!