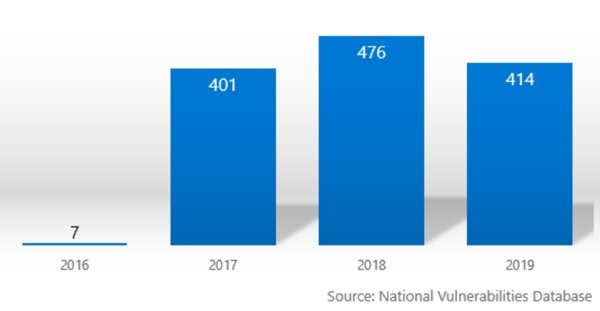
Firmware attacks have been known for many years. However, in recent times, the attacks have increased by a huge number. According to NIST’s National Vulnerability Database, nearly a five-fold increase in the number of firmware vulnerabilities has been discovered in the last three years.
Considering such a scenario, Microsoft is launching new device security requirements that can tackle the targeted Firmware attacks.
New security requirements against Firmware attacks in Microsoft Device
In recent years, due to increased security research, malware attacks and other vulnerabilities have been addressed to a maximum extent. Software companies are proactively building protections into the OS and the connected devices. As a result, attackers are now looking for other options for exploitation and firmware attacks are emerging as the latest target.
Firmware lies in the core of any device as it is used to initialize the hardware and other software on the device. Firmware has a higher level of access and privilege than the hypervisor and operating system kernel. Hence, firmware attacks are becoming a top-most choice for the attackers.

Microsoft, along with its partners announced a new initiative called Secured-core PCs. As Microsoft describes, these devices meet a specific set of device requirements. These requirements apply the security best practices of isolation and minimal trust to the firmware layer, or the device core, that underpins the Windows operating system. The data-sensitive industries such as financial services, government, and healthcare as well as the workers that handle highly-sensitive IP, customer or personal data are some of the users who would need such devices.
Features of a Secured-core PC
As Microsoft describes, Secured-core PCs combine identity, virtualization, operating system, and hardware and firmware protection to add another layer of security underneath the operating system. Unlike software-only security solutions, Secured-core PCs are designed to prevent these kinds of attacks rather than simply detecting them.
Way before the implementation of Secured-core PCs, Microsoft had started implementing solutions to remove trust from the firmware. Thus, Microsoft had already started implementing security measures against firmware attacks. Microsoft had introduced Secure Boot to mitigate the risk posed by malicious bootloaders and rootkits that relied on Unified Extensible Firmware Interface (UEFI) firmware. This way only the properly signed bootloaders like the Windows boot manager to execute were allowed.
David Weston, Partner Director, OS Security mentions in his article about Secured-core PCs,
“Our investments in Windows Defender System Guard and Secured-core PC devices are designed to provide the rich ecosystem of Windows 10 devices with uniform assurances around the integrity of the launched operating system and verifiable measurements of the operating system launch to help mitigate against threats taking aim at the firmware layer. These requirements enable customers to boot securely, protect the device from firmware vulnerabilities, shield the operating system from attacks, prevent unauthorized access to devices and data, and ensure that identity and domain credentials are protected.”
It is really a well-thought step taken by Microsoft. In the scenario where there is an increase in cyber-attacks that are smart and difficult to identify easily, Microsoft’s Secured-core PCs will help users protect their data more effectively. Read more information about Secured-core PCs and firmware attacks on Microsoft Security blog.
Leave a Reply