Duo Labs recently did a complete security analysis of OEM updaters that come with theWindows machines by default. Their study found out the many of the PC manufacturers come with preinstalled updater that can make the system vulnerable. Duo Labs calls this study ‘Out of Box Exploitation’. Here’s a quick look at what the Out of Box Exploitation study covered and how threatening the OEM updaters can be.
Out of Box Exploitation
The name of the study is derived from OOBE or Out of Box Experience. It is nothing but the first time experience any user has, when he uses a new computer or device. The OOBE includes the setup process of installing and performing initial configuration of a hardware or software on a computer. Every computer manufacturer wants to offer the best OOBE to the new user. However, it seems the pre-installed updaters have changed the meaning of OOBE to Out of Box Exploitation.
The researchers call the OOBE as ‘Out of Box Exploitation’ because many computers these days come with the bloatware. Bloatware or the Crapware are the pre-installed software that are unwanted. And these very bloatware make the PC vulnerable to malware and virus attacks. The process of OOBE varies from one OEM vendor to another; however, the experience remains the same. Users need to wait for
The process of OOBE varies from one OEM vendor to another; however, the experience remains the same. Users need to wait for pre-loaded software to start up and force you to click through product registration and 30 days trial prompts.
What gives rise to Out of Box Exploitation
According to the researchers of Duo Labs, the incidents of Out of Box Exploitations take place due to some of the missing security features in the OEMs. The researchers mention in their report,
“Every single vendor had at least one vulnerability that could allow for a man-in-the-middle (MITM) attacker to execute arbitrary code as SYSTEM. We’d like to pat ourselves on the back for all the great bugs we found, but the reality is, it’s far too easy.”
They also published the basic features from some of the updaters:
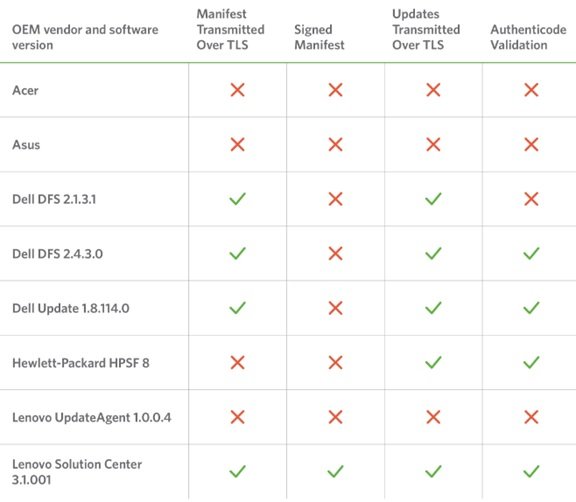
The typical concerns found by the researchers from Duo Labs regarding Out of Box Exploitation are as follows:
- Every vendor shipped with a preinstalled updater that had at least one vulnerability resulting in arbitrary remote code execution as SYSTEM, allowing for a complete compromise of the affected machine.
- Vendors often failed to make even basic use of TLS, properly validate update integrity, or verify the authenticity of update manifest contents.
- Vendors sometimes had multiple software updaters for different purposes and different implementations; some more secure than others.
- The large attack surface presented by ancillary OEM software components makes updater-specific bugs easier to exploit in practice by providing the missing pieces of the puzzle through other tools bundled with their systems.
You can read their blog and the complete report to know more about Out of Box Exploitation.
Leave a Reply