In a surprising move, developers of TeslaCrypt ransomware have made their malware defunct. The developers of the ransomware have changed the message on their last operation site and rendered an unconditional apology for the inconvenience caused to all whose data they had encrypted. To decrypt the TeslaCrypt Ransomware encrypted files, a solution too, has been offered on the website.
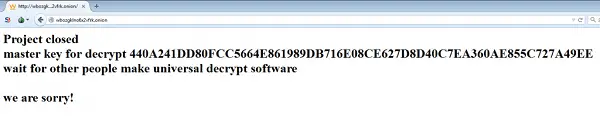
TeslaCrypt ransomware is defunct
TeslaCrypt was in the news a year earlier for claiming ransom money from users for decrrypting the files it encrypted. On May 18th, the TeslaCrypt developers announced on their TOR site that the TeslaCrypt ransomware was closed and alongside the announcement released the master decryption key.
TeslaCrypt developers have now started recommending that affected users employ TeslaDecoder to decrypt their files. The tool also has been updated to recover the encryption key for all TeslaCrypt variants.
How does TeslaDecoder function
The tool tackles the master private key that TeslaCrypt used on the victim’s computer, thus allowing users to decrypt all files. The tool is designed to run particularly on Windows OS and does not require specific encrypted file types. This ability of the tool makes suitable for general use.
Please note that, TeslaDecoder cannot be used in combination with specialized factorization tools. There can be two reasons for the sudden departure from usual behaviour,
There can be two reasons for the sudden departure from usual behaviour, and why this was done:
- By turning in the decryption key, the ransomware developers are hoping to escape from the radar of the law enforcement agencies.
- Ransomware criminals rely on their reputation of actually releasing the data in order to entice victims to pay.
What do you think could be the reason?
Leave a Reply