A new ransomware called as “Threat Finder” has been discovered by a security researcher at Rackspace. Threat Finder is feared to be a copy of Cryptolocker and can infect Windows PC’s via multiple sources; the most common infection is when a user browses a compromised website.
Threat Finder’s discovery means that online community is exposed to a fatal malware that targets personal files and folders, encrypting them and asking ransom for decryption. Also, it reaffirms the fact that Cryptocker ransomware was indeed never eliminated. On the contrary, it was just waiting to resurface with another name.
Threat Finder Ransomware
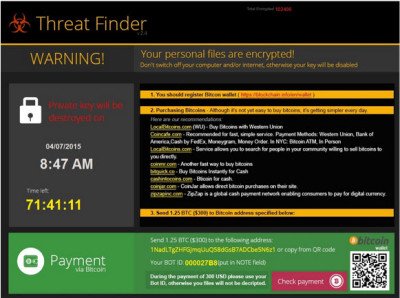
Threat Finder was reported in January 2015 by security researchers. Brad Duncan, the Security Researcher at Rackspace, came across the ransomware on Tuesday, April 7th, 2015 when it infected a Windows host.
Brad says that the host was infected when casual web browsing led to the Angler exploit kit. After the infection, the host’s personal files were encrypted, and instructions for Threat Finder v2.4 appeared on the desktop screen.
An example of a successful Threat Finder attack:
- Step 1: The user viewed a compromised website that generated behind the scenes traffic for Angler exploit kit.
- Step 2: The vulnerable Windows host was infected by the Angler exploit kit.
- Step 3: The exploit kit sent Bedep malware, commonly seen from Angler [3].
- Step 4: Bedep downloaded more malware, including Threat Finder.
- Step 5: Threat Finder encrypted the user’s personal files and displayed instructions to recover the data.
On a successful attack, the infected host computer contains at least one registry entry for a file named reg.dll.
Further analysis by Rackspace.com revealed that, reg.dll generated traffic to 65.49.8.104, sending approximately 217 KB of data to the infected host. The analysis shows dropped files that are images for Threat Finder’s decrypt instruction. Threat Finder asks ransom via Bitcoin, however, there is no certainty that attackers would give decryption code after they receive the money.
What you should do when infected with Threat Finder
Sadly, there is no such trick to save your personal folders once you are infected with this dangerous malware. The only solution to save your data is to take timely backups and take the usual steps to Prevent Ransomware from getting onto your computer.
The prevention apps your story’s conclusion contains links to are fairly good at stopping ransomware; Chrome users might also like to know about an extension called “Dr. Web Anti-Virus Link Checker” I’ve been testing (as a purely self-interested, non-employee/contractor party) for a week.
The said extension has been working for me with yet no known false positives, nor any false “go-aheads”. I’ve tested it against EICAR links, known malware links, known or suspected (e.g., Phishtank) phishing links, and so on. Whether via corporate or public (e.g., GMail) email links, similar conditions, similar good extension results.
The last test I gave was to first ensure a site for a certain well-known screen capture program would deliver !Artemis via installer; sure enough, my PC got browsers changed to Smart Fox, Dregol, and other nastiness; I removed it all after hours, tested and re-tested for return to normalcy, then uploaded the installer file to VirusTotal…yes, !Artemis is in it, but only 8 of over 50 scanners could see it, Dr. Web being one of them. I then had the Dr. Web extension check the download link back at the source, and it correctly warned of the infection lurking.
I hope this is of use to those using Chrome in further avoiding bad things at the end of any email or web links; cheers!
Yes, Dr. Web Anti-Virus Link Checker is a good Website URL Scanners & Link Checker addon for your browser.