The latest information on global threat from malicious websites and shady IP addresses can, in fact, help a company detect threats and rapidly respond. The challenge is that threat intelligence feeds are, at best, uneven in quality.
According to analysis by top information security professionals, almost 70% of these threat intelligence feeds are sketchy and not dependable in terms of quality. They claim that only 31% of the entire spectrum is accessible and accurate. This low success rate means that IT staff will have to focus on manual vetting and shuffling of the data. With more than 17,000 malware threats detected every week, this unnecessary process takes up majority of the time of most IT professionals.
So, better and more accurate data is the key to reducing this excessive human effort. These three key areas are helpful in achieving the results.
- Increase the diversity, scale, and variety of data
- Implement machine learning and behavioral analytics
- Utilize simple tools that make mitigation more efficient.
Microsoft Threat Intelligence
This component of Microsoft’s risk analysis department gathers data from across all of the company’s products and services. In addition to this, between their Digital Crimes Unit (DCU), Cyber Defense Operations Command Center (CDOC), and the entire organisation, Microsoft employs thousands of the smartest security experts to protect sensitive products like Azure and Office 365.
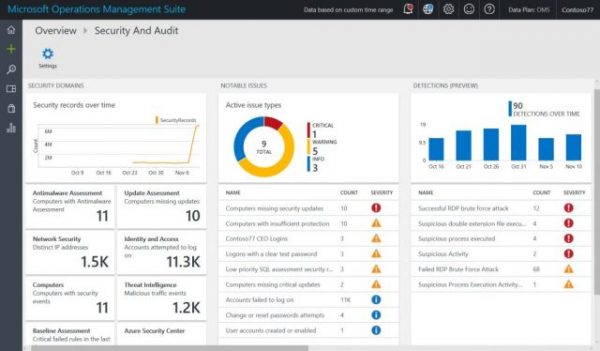
The Operations Management Suite collects data from across datacenters—Windows, Linux, Azure, on-premises, and AWS—and correlates it with the latest Microsoft threat intelligence to detect attacks targeting your organization. Not a list that is days old, but one that is updated in real time. It also applies behavioral analysis and anomaly detection to identify new threats, which align to known patterns of attack. Users are provided with a list of the most pressing issues, immediately actionable and conveniently prioritized by the potential threat they pose.
For a detailed read visit Microsoft.
Leave a Reply