A new TorrentLocker form called as Crypt0L0cker has been detected in parts of Asia, Europe and Australia. Crypt0L0cker is a ransomware and derives its name from another popular ransomware CryptoLocker. The noticeable difference between the two names is that the o’s are replaced with 0’s (zeros).
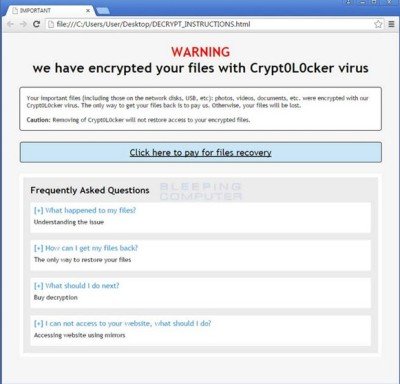
Crypt0L0cker is very much like its predecessor TorrentLocker in terms of attack. However, additionally, Crypt0L0cker adds .encrypted extension to the file name it infects. Once successful, it leaves, HTML ransom note as DECRYPT_INSTRUCTIONS.html and text version as DECRYPT_INSTRUCTIONS.txt.
Crypt0L0cker works like most other Ransomwares. It attacks PC’s and encrypts personal files and folders. Post successful infection, it demands ransom in the form of online currencies, such as BitCoin to recover encrypted files.
Crypt0L0cker ransomware has a unique way of infecting
Crypt0L0cker is currently circulating in the form of emails that pretend to be traffic violations or other government notices. Based on the similar script of TorrentLocker, it connects to a Command & Control server and send the victim’s unique identifier as well as the campaign ID. The Command & Control server then sends back a text or an HTML ransom note.
Until now, Crypt0L0cker hasn’t been the most talked about Ransomware threat. But, this doesn’t mean that it is a feeble threat at all. On the contrary Crypt0L0cker is the most intelligent threat of all the Ransomware. Unlike TorrentLocker or CryptoLocker who have a well-defined attacking list, Crypt0L0cker doesn’t have a list and that is something which makes it deadlier. Crypt0L0cker starts by scanning all hard drive letters and encrypt any files that do not match an exclude list.
Crypt0L0cker has a hard coded list of extensions that it does not target. Hence this unique algorithm allows it to encrypt any file type other than the selected few that it deems would cause a problem with Windows, says BleepingComputer. Hence even if a user is smart enough to save files in an unusual format thinking it won’t be detected, Crypt0L0cker infects that file too. It also deletes shadow files of the volume to ensure that you don’t recover your files.
Currently there is now way to protect yourself from this ransomware. Taking regular backups however is always recommended.
Leave a Reply