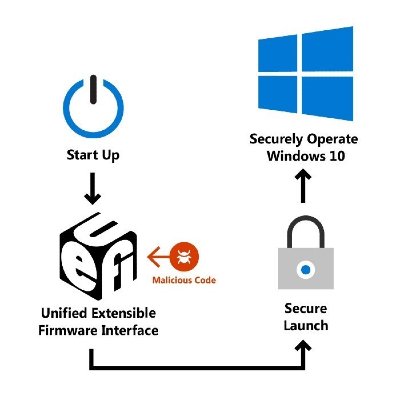
Microsoft has outlined a new Secure Launch mechanism to safeguard PCs against malicious firmware code. Secure Launch on Windows 10 is designed to safeguard your PC against sophisticated boot attacks. At first, it allows the execution of untrusted code during the boot process but then it takes control of the CPU processes so that the system is successfully launched into a trusted state. The core functionality of the Secure Launch is to filter out early Unified Extensible Firmware Interface (UEFI) code from the trust boundary.
What is Secure Launch?
Windows 10 has so many built-in features to prevent advanced hardware and firmware attacks. But for these features to work as intended, Microsoft says the platform’s firmware and hardware must be trustworthy and healthy. A trusted source encrypts every component in the boot process for validation purposes. If attackers tamper with those components, they could gain unauthorized control over Windows 10 security features that use the firmware and hardware.
This is where the Secure Launch comes in handy. In its recent blog post, Microsoft said:
“Secure Launch is the first line of defense against exploits and vulnerabilities that try to take advantage of early-boot flaws or bugs. Firmware enclaves and built-in silicon instructions allow systems to boot into a trusted state by forcing untrusted, exploitable code down a specific and measured path before launching into a trusted state.”
How Secure Launch on Windows 10 works?
Divided into two phases, the first phase in the Windows boot environment runs with UEFI and benefits from boot services considered untrusted for Secure Launch. During the second phase, the trusted portion runs in the absence of firmware services. The second phase (trusted phase) only runs a portion necessary to perform a Dynamic Root of Trust Measurement (DRTM) event.
Secure Launch on Windows 10 safeguards Secure Management Mode
Ensuring the safety of System Management Mode (SMM) is of paramount importance. Well, the SMM handles power management, hardware configuration, thermal monitoring, and more. Hence, if an attacker can exploit SMM, they can easily bypass some of the checks in Secure Launch or even worse, they can also exploit the runtime operating system. Thanks to Secure Launch, Windows 10 PCs can detect when SMM is trying to access a critical platform resource such as memory, IO, or certain CPU registers.
Secure Launch works well with support for components, as follows:
- Intel, AMD, or ARM virtualization extensions
- Trusted Platform Module (TPM) 2.0
- On Intel: TXT support in the BIOS
- On AMD: SKINIT package must be integrated in the Windows system image
- On Qualcomm: Implements DRTM TrustZone application and supports SMC memory protections.
- Kernel DMA Protection
On secured-core PCs, System Guard Secure Launch with SMM Protection is enabled by default.
Leave a Reply