Barely, has the fear about WannaCrypt Ransomware subsided, comes the news that even before WannaCrypt, there was this UIWIX Ransomware that was also exploiting SMB Vulnerabilities. The newly discovered malware assigns a unique machine ID to each infected computer by encrypting all of its data and renaming it with the “._.UIWIX file extension”.
UIWIX Ransomware exploits SMB Vulnerabilities
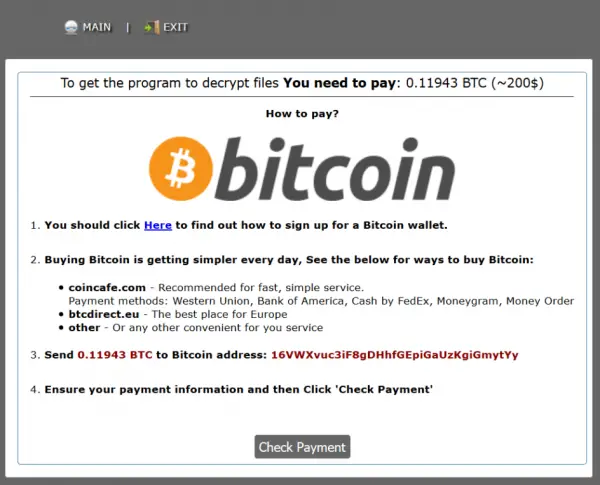
Following the infection and encryption process, the UIWIX file virus drops behind a ransom note, named as “_DECODE_FILES.txt”. The ransom-demanding message prompts the victim to transfer 0.12261 Bitcoins by entering a Tor-based website. Here’s a snapshot of it given below.
>> ALL YOUR PERSONAL FILES ARE DECODED <<< Your personal code: [% unique ID%] To decrypt your files, you need to buy special software. Do not try to decode or modify files, it may be broken. To restore data, follow the instructions! You can learn more at this site: https://4ujngbdqqm6t2c53.onion [.] two https://4ujngbdqqm6t2c53.onion [.] cab https://4ujngbdqqm6t2c53.onion [.] Now
After you start the Tor browser you need to open this link http //4ujngbdqqm6t2c53[.]onion
The modus operandi of the trojan is similar to other ransomware i.e., it encrypts the files of the victim and asks them to pay a ransom in exchange for the decryption key. The payment gateway charges 0.11943 Bitcoins which is equivalent to $218.
Even if the payment is transferred, there is no guarantee in this case as the attacker may take your money while still leaving you with all your files still encrypted.
This ransomware attack has become so extensive because it abuses various security holes in Windows SMBv1 and SMBv2, which most users have left unpatched, in spite of the critical update released by Microsoft in March 2017, says Heimdal.
The only way to mitigate this emerging threat at the moment is to patch the affected operating systems and keep the anti-virus protection ‘ON’ against it. This is the most tried and tested method to avoid damages from Ransomware attacks.
Leave a Reply