A component of the Kaspersky Internet Security was found to be preventing its users getting timely security updates or browsing even the safe websites. The component of the antivirus called as the “Network attack blocker” can actually be exploited by the attackers allowing them to force the antivirus blacklist any host address which could be anything starting from a Windows update to any other web address.
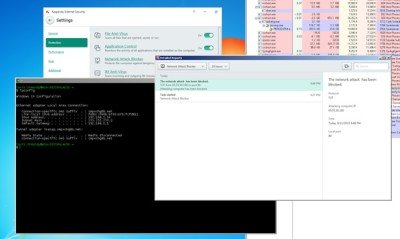 This security vulnerability in Kaspersky Internet Security was discovered by Tavis Ormandy from the Google’s Project Zero team who could find a couple of security flaws in the antivirus design.
This security vulnerability in Kaspersky Internet Security was discovered by Tavis Ormandy from the Google’s Project Zero team who could find a couple of security flaws in the antivirus design.
Tavis said,
“There are two obvious weaknesses in this design”
-
It is not possible to differentiate between a sequenced TCP packet and an unsequenced TCP packet, therefore it is possible to spoof the origin.
-
It is not possible to determine the application layer state when the packet was received”.
Vulnerability in Kaspersky software
First of the two, Kaspersky users may not get crucial software updates like Windows security updates or any other application update. Tavis explains that an attacker may simply extract a signature and send it to a Kaspersky user with a spoofed source address that actually forces the antivirus application to blacklist any host. This happens because the associated component of the antivirus app is merely a simple stateless packet filter with a pattern-matching signature system. It has no concept of flow reassembly or protocol decoding, which require stateful packet inspection.
Therefore, instead of carrying out a thorough inspection, when the software detects an attack, it adds the source address to an IP blacklist preventing any further communication with the host.
Blocking servers which aren’t really a threat
The second attack which exploiters may employ is a simple one. They just have to paste a signature into an email, or embed a signature into an image prompting Kaspersky Internet Security antivirus to block it which means that the user can no longer communicate with their mail server.
Again the component structure is responsible as a stateless packet inspection cannot understand the higher layer protocol state, because of the lack of context. Hence the inability to differentiate weather the incoming data is an email or comment may actually result in blocking mail servers which shouldn’t be blocked.
Kaspersky lab is learnt to have issued a fix on October 8.
Leave a Reply