The last several hours have been the dark hours for various organizations worldwide. A massive Ransomware attack has hit tens of thousands of computer systems in various companies and organizations across several countries including the UK, China, US, Russia, Italy, Spain, Vietnam, and Taiwan.
Initiated as an NHS cyber-attack this ransomware soon turned into a worldwide cyber-attack. This is a one-of-its-kind massive attack and as per the latest updates from Jakub Kroustek at Avast security firm tweeted about the attack. As of writing, it is estimated that there have been over 75,000 infections in 99 countries in the past 12 hours.
UPDATE: It is now 230,000 computers in 150 countries and counting.
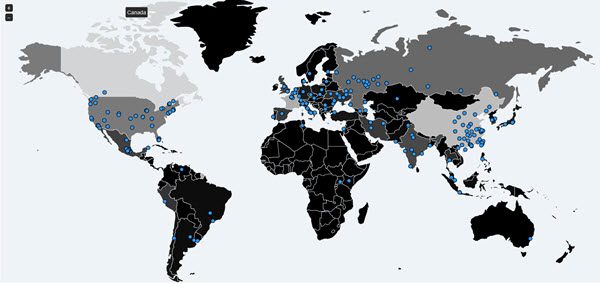
The real-time Malwaretech malware tracker shows that the infections is rising and has now even spread to India and China – and South America & Africa too.
However, it is still not officially confirmed if these attacks were connected. Starting with hospitals, this huge ransomware attack termed as WannaCry or Wcrypt or WanaCrypt0r has hit several other companies including some leading banks, national health services and telecommunication giants. Telecoms companies like Portugal Telecom, Megafon and Telefonica, power firm Iberdrola, utility provider Gas Natura, FedEx, and many others have been affected.
Kurt Baumgartner, the principal security researcher at Kaspersky Lab states in a report, “Effected machines have six hours to pay up and every few hours the ransom goes up. Most folks that have paid up appear to have paid the initial $300 in the first few hours.”
What is WannaCry Ransomware
WannaCrypt0r also termed as WannaCry and Wcry or Wcrypt is one of the biggest ever ransomware attack which has by far infected thousands of Windows systems worldwide. The ransom asked against the decryption key starts with $300 Bitcoin which increases after every few hours. The attackers are reportedly using Microsoft Windows exploit ‘Eternal Blue’. These tools have been reportedly stolen and misused by a group called Shadow Brokers.
EternalBlue is a hacking weapon developed by NSA to gain access and command the computers running Microsoft Windows. It was specifically designed for the America’s military intelligence unit to get an access to the computers used by the terrorists. The tool was stolen earlier this year and Microsoft was warned by NSA regarding the same, following which the Company released a patch in March allowing computer users to update their systems. The possibility of outdated PCs at NHS being vulnerable to the attack can’t be denied in such scenario.
The WannaCry ransomware changes the affected file extension names to .WNCRY, encrypts the files and then drops a ransomware note demanding payment of a ransom amount. The wallpaper is also changed.
However, it is still not proven if EternalBlue is the only tool used by the attackers or they are propagating through some other sources too. The malware is reportedly one the most virulent ones and unfortunately, the initial infection vector is still not identified by the security firms. The malware has completely crippled the network of many hospitals, telephonic companies, and government organizations and still counting.
Precautions to take
The malware is still spreading and is believed to be the biggest cybersecurity incident by far after the CodeRed attack which compromised 359,000 PCs in 2001. Apart from taking the usual precautions to prevent Ransomware, Windows users are recommended to be extremely careful about clicking the web-links or opening the email attachments. Microsoft has also suggested installing MS17-010 right away to stay safe.
Microsoft has also released emergency WannaCry patches for non-supported operating systems like Windows XP, Windows 8, Windows Server 2003. Make sure you patch your system right away!
You may also make use of these WannaCry Ransomware Protection Tools.
Customers running Windows 10 were not targeted by the attack.
UPDATE: Security researcher accidentally stops WannaCry Ransomware outbreak.