A report from Check Point Security Research suggests that Subsystem for Linux (WSL), a newly introduced feature in Windows 10 ( a hybrid concept which allows a combination of Linux and Windows systems to run at the same time) could be used to force a malware into Windows system as Bashware.
Windows Subsystem for Linux recently graduated from its Beta stage to become a fully supported Windows feature. However, the security solutions existing for it have not yet been adapted as to monitor processes of Linux executables running on Windows. As such, it can be exposed to unnatural attacks.
Elbaz and Atias, members of Check Point Security Research, said,
This may open a door for cyber criminals wishing to run their malicious code undetected, and allow them to use the features provided by WSL to hide from security products that have not yet integrated the proper detection mechanisms.
Bashware leverages Windows Subsystem for Linux for Malware Attacks
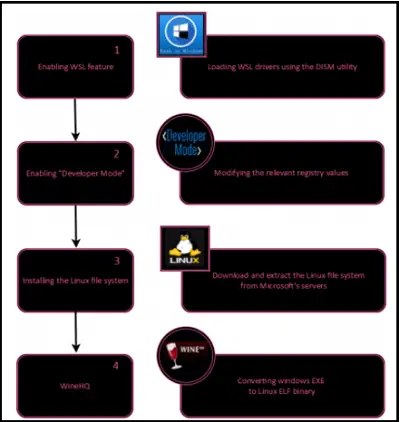
Bashware is a generic and cross platform technology that uses WSL in order to allow running both ELF, an EXE malicious payloads in a stealthy manner that could bypass most current security solutions. It is found that Bashware loads the malicious payloads in 4 major steps that can be summarized below as,
- Loading WSL components
- Enabling developer mode
- Installing Linux
- Wine.
When completed in order, the Bashware becomes a perfect demonstration tool for running any malware undetected, bypassing the most common security products – anti-viruses, inspection tools, debugging tools, etc, reports CheckPoint.
https://youtu.be/4ki6dbEePaw
Microsoft has acknowledged this problem and already taken steps to help security vendors deal with such attacks. It advises users to enable developer mode (Developer mode is not enabled by default), then install the component, reboot, and install Windows Subsystem for Linux in order to remain safe.
Leave a Reply