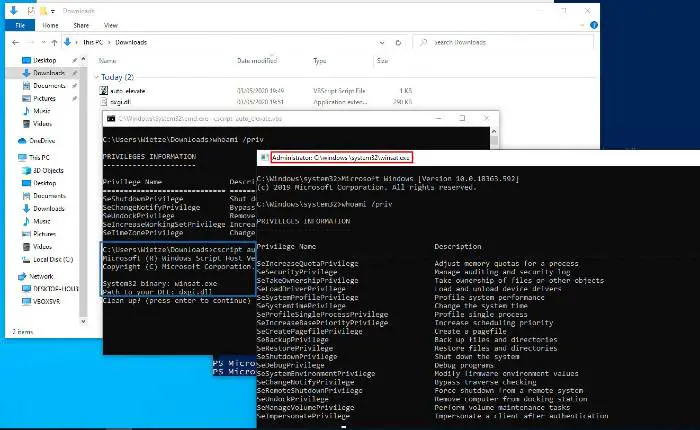
Almost 300 executable files in the System32 folder of the Windows 10 operating system are vulnerable to DLL Hijacking, claims a security researcher Wietze Beukema. According to Beukema, a simple VBScript can make these executables vulnerable to DLL Hijacking, entirely bypassing User Account Control (UAC).
System32 folder vulnerable to DLL Hijacking
First, let’s try to understand what is DLL. In the context of Windows 10 in particular, DLL stands for Dynamic Link Libraries. They are the external components of the operating system. The Dynamic Link Libraries store codes for other applications. DLL files are loaded into RAM only when required. As a result, they serve as extensions to different applications, thus saving memory.
In DLL Hijacking, attacker invokes third-party code by replacing an authentic code library with a tampered one or dropping a malicious payload on the search path. This way, attacker circumvents User Account Control in an attempt to drop a malicious payload onto a victim’s computer.
In this case, attackers could resort to relative path DLL Hijacking. This method involves copying the legitimate application to a user-writeable folder alongside the malicious DLL.
As Beukema illustrates, the biggest difficulty is to discover a vulnerable executable that can be exploited under default user permissions. The relative path is the weakest variant of DLL Hijacking.
The malware embedded the legitimate software and dropped it to disk has to be the result of copying the legitimate executable from Windows 10’s System32 folder. But it only works with vulnerable or unpatched executables.
“To prevent new versions of this technique to be successful, it is worthwhile identifying executables that are vulnerable to this kind of DLL hijacking.”
During his research, Beukema found 616 executables in Windows 10 v1909 vulnerable to relative path DLL Hijacking:
“Some applications come with a GUI, or some other visual element that gives away the binary was executed. This also includes error messages: required DLLs might be missing, and the hijacked DLL obviously lacks the original functionality. Attackers are less likely to target such applications for DLL hijacking purposes.”
How to prevent DLL Hijacking?
A simple method would be using absolute paths instead of relative ones. But since this is not possible for all applications, the better option is to verify all DLLs before loading them.
Earlier this month, cybersecurity researchers discovered a DLL Hijacking method employed by the Metamorfo malware campaign that primarily targets financial firms. Attackers were caught using reliable software components to compromise the computers, courtesy of DLL Hijacking.
Leave a Reply