Windows Defender recently prevented a crypto mining malware epidemic from spreading to millions of PCs across the World. The trojan, known by the name – Dofoil or Smoke Loader, had plans to deliver a range of coin miner payload on the victim’s PC when it was detected by Windows Defender.
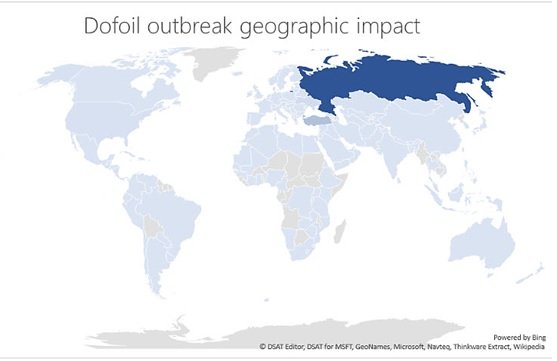
Microsoft first spotted the campaign when its Windows Defender Antivirus blocked 80,000 attacks thanks to its inbuilt behavior monitoring and machine learning capabilities. More than 400,000 were about to be infected before Windows Defender stuck over a 12-hour period. The attacks were mainly concentrated in Russia (73% detections), Turkey (18% detections) and Ukraine (4% detections).
However, in this case, it dropped a cryptocurrency miner on infected PCs, in order to earn those behind the trojan Electroneum coins from victims’ CPUs.
How Dofoil or Smoke Loader infects
- Dofoil spreads by implementing ‘process hollowing’ on the legitimate explorer.exe binary. (Process hollowing is a code injection technique that involves spawning a new instance of a legitimate process and then replacing the legitimate code with malware).
- The second phase of this crypto mining malware attack involves dropping the coin-mining malware, which as part of a well-thought disguise appears like a legitimate Windows binary wuauclt.exe. Although, Dofoli is capable of generating a variety of cryptocurrencies, in this case, it creates Electroneum.
- To stay hidden, Dofoil modifies the registry. The hollowed explorer.exe process creates a copy of the original malware in the Roaming AppData folder and renames it to ditereah.exe. It then creates a registry key or modifies an existing one to point to the newly created malware copy. For instance,
Win32/Dofoil may copy itself to the Windows startup folder, for example:
- <startup folder>\dxdiag.exe
- <startup folder>\lxdiag.exe
- <startup folder>\ctfmon.exe
- <startup folder>\gefreg.exe
Note: <startup folder> refers to a variable location that is determined by the malware by querying the Operating System. The default installation location for the Startup folder for Windows 9x, Me, NT, 2000, XP and 2003 is ‘%USERPROFILE%\Start Menu\Programs\Startup’. For Windows Vista and 7, the default location is ‘%USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup’.
It sets the “read-only” and “system attributes” for its copy.
Some variants may also copy themselves in the %appdata% folder using the same file names as legitimate Windows files, for example:
- %appdata%\csrss.exe
- %appdata%\smss.exe
Dofoli can also infect via emails
Dofoil can also strike via emails, arriving at the victim’s PC through attachments often embedded as Macros in Microsoft Word documents. The following are examples of file names used for the attachment:
- New_Password_IN46537.zip
- Invoice_Copy.zip
- Facebook_Password.zip
An antivirus is essential, and there are browser extensions that block web pages from loading cryptocurrency mining software, but the best way to protect yourself is caution – don’t open attachments in unexpected emails and always check URLs before clicking.
More Crypto mining threats arriving?
With interest in cryptocurrencies growing exponentially, malware managers see this as an opportunity to include crypto mining malware components in their attacks with more and more exploit kits delivering coin miners instead of ransomware. And with the arrival of Dofoil, it has only become easy to forecast that Cyber criminal groups are actively developing their methods and looking to implement more sophisticated techniques to spread mining software in the near future, says Microsoft.