Carnegie Mellon University which operates the Software Engineering Institute (SEI) for the U.S. Department of Defense has published an article about a vulnerability in the Windows Task Scheduler. The Task Scheduler uses a function SetJobFileSecurityByName. According to the original finder, the zero-day attack can be triggered by using the legacy task format.JOB with the recent version of Windows.
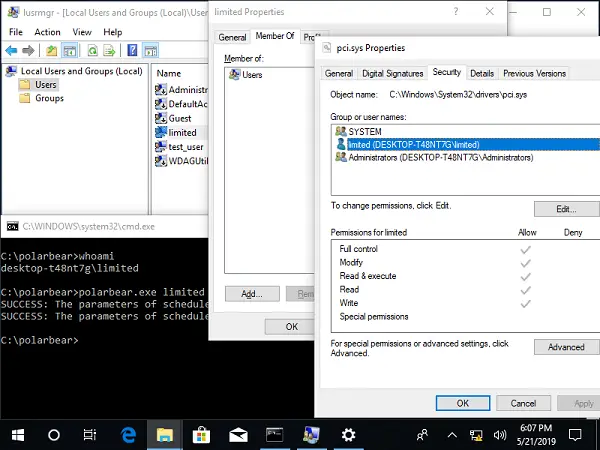
Will Dorman was able to reproduce the issue by recompiling the code on 64-bit Windows 10 and Windows Server 2016 and 2019. The image above shows how the Task Scheduler imported via command line have full access after the import is complete. However, the user doesn’t have full permissions.
Windows Task Scheduler Privilege escalation vulnerability (Zero-Day)
So how does this happen? When legacy files are imported using the existing Task Scheduler, SetJobFileSecurityByName function sets full user access permissions to data. It is because the Task Scheduler service has the NT Authority\SYSTEM security token. The problem occurs because there is no correct DACL maintained for imported JOBS.
As per SEI-
In conjunction with the SYSTEM security token used by the Task Scheduler service, this migration behavior can be used along with hard links to grant full permissions of protected files to any user on a Windows system.
The vulnerability affects both 32- and 64-bit fully-patched Windows 10 platforms, as well as Windows Server 2016 and Windows Server 2019. Windows 7 and Windows 8 doesn’t have this issue.
The severity is very high, and the attacker can gain full access to protected files. It means that the complete system can be compromised. On top, if the user account doesn’t have admin privileges, it still works.
No statement is currently available from Microsoft, regarding this vulnerability, state cert.org.
Leave a Reply