We have new ransomware in town called ZeroLocker. Ransomware are considered as a get-rich quick tool by malaware writers these days. ZeroLocker encrypts all your data including files with AES encryption key once it is done, it display a message to pay via Bitcoins to decrypt computer files.
ZeroLocker ransomware
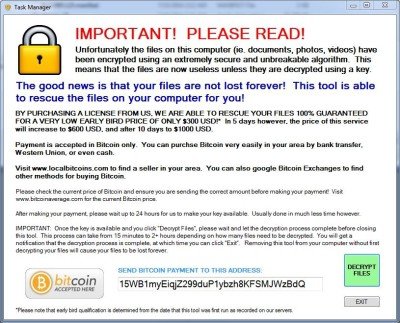
The workflow of ZeroLocker tool is totally different as compared to any other ransomware, as it encrypts all files under windows C: drive which includes all executable files. Once the file are locked by the tool it adds extension to the file as .encrytped. The file names which include the keywords Desktop, Windows, Program files, ZeroLocker are however safe and are not encrypted.
In the beginning, users won’t even realize that they have installed such application as it appears to them as an authentic de-encryption tool. It presents itself as a Helper Tool that had discovered encrypted files on your system and is trying to help you. But, in reality it’s not, as quoted by security expert ZeroLocker is considered as the most destructive tool designed till date.
After the encryption is completed, it runs a file stored under C:\Windows\System32\Cipher.exe /w:C:\ command, this command overwrites all deleted data hence provides no room for data recovery software to recover those deleted files. However users can run system restore point along with Windows built-in previous version or Shadow Explorer to recover the files which are not infected by ZeroLocker.
The ransomware stores ZeroLocker.exe under C:\ ZeroLocker folder which is a decrypt executable file which executes as soon the computer starts. The decryption key used to unlock the program are stored to Command and Control Server. When a private key is uploaded to the Command and Control Server, it returns HTTP 200 error – but unfortunately even when ZeroLocker tries to upload those private key it returns HTTP 400, as the requested page doesn’t exist on the server.
Hence, those keys to remove ZeroLocker are not stored in any database, files or folder for recovery. This ransomware can only be decrypted by manually filter through HTTP access logs, reports BleepingComputer. Due to lack of proper decryption tool even a victim pays through Bitcoin, they won’t be able to get decryption key as it doesn’t exist anywhere – hence it is considered as very destructive ransomware!
There are a few steps you can take to take to stay protected & secure and Prevent Ransomware from getting an entry into your computer. You ay want to check the post out.
Leave a Reply