Managing passwords can be a tricky thing, especially now that everyone has accounts on so many services on the internet. Due to this, the same password gets used in multiple accounts. On top of that, many users use a password that has a similar pattern and is used with slight modification. According to the report, nearly 30 million users and their passwords, password reuse, and modifications were common for 52% of users. Even worse, Microsoft reports that 44 million use leaked passwords on Microsoft Accounts.
44 million use leaked passwords on Microsoft Accounts
The study that revealed 2018 stats also revealed 30% of the modified passwords, and all the reused passwords can be cracked within just ten guesses. That is alarming. Imagine you using the similar password of the most crucial account of yours getting cracked open in ten guesses. It’s no joke that every online service asks you to create a unique password for their accounts.
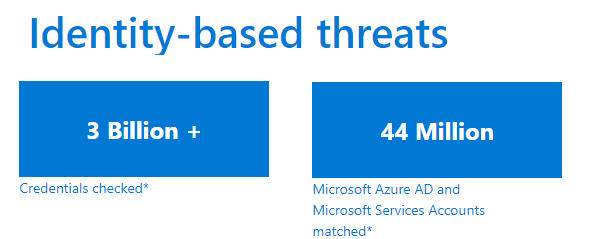
As per the latest report from Microsoft on password, where they checked millions of credentials obtained from different breaches, 3 billion credentials, and found a match for over 44 million Azure AD and Microsoft Services Accounts. Microsoft team does this check against the accounts on their services, and force a password reset to protect them. While this on the consumer side, Microsoft sends out an alert to IT admins for Enterprise customers. If alerted on time, they can perform a force reset for their accounts.
Microsoft offers Azure Active Directory Identity Protection tool that automates the detection and remediation of identity-based risks, investigates risks using data in the portal, and export risk detection data to third-party utilities for further analysis.
Multi-Factor Authentication is important
While not everyone can be forced not to use the same or similar passwords, one thing can be forced MFA or Multi-Factor Authentication or 2FA. It adds another layer to account security with codes that can be generated either by sending an OTP to the mobile number or using Authenticators. Microsoft reports:
Our numbers show that 99.9% of identity attacks have been thwarted by turning on MFA. You can learn about Microsoft Azure MFA here. Microsoft also offers solutions to protect customers from breach replay attacks. This includes capabilities to flag users as high risk and informs the administrator to enforce a password reset.
Breach replay attack
The study also found that re-used and modified passwords also put users at risk of being victims of a breach replay attack. In this attack, the attacker uses the same password on different accounts to check if there is a match. One of the common habits among users is to get the same account name or email id everywhere. If a password of your account is leaked, the attacker will try to use the same password assuming the same user name or email ID on another service. If the victim had used the same password, it would be hacked.
Leave a Reply