After discovering a potential security vulnerability in the current version of Java (Java 7 update 10) Mozilla added it to the add-on block list. Now, Apple seems to be following suit. The company on Thursday quietly disabled Java 7 on its Mac machines that already had the plug-in installed.
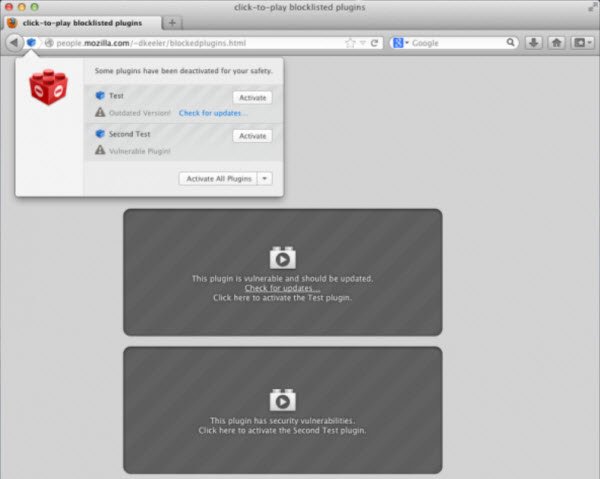
As per some reports, the vulnerability was being actively exploited by the attackers, capable of affecting any browser that had the Java plugin installed. Realizing this, Mozilla added the plug-in to its add-on block list however, it still allowed users to run the plug-in if needed. Apple on the other hand, took a different approach. The company completely blocked Java 7.
It did so by updating “Xprotect.plist” blacklist to require a minimum of an as-yet unreleased 1.7.0_10-b19 version of Java 7, points out Mac Rumors. The devices running currently publicly available version of Java – 1.7.0_10-b18, are failing to pass the built-in anti-malware system check, marking Java 7 as malware.
Earlier, Apple provided its own support for Java on OS X. Since October 2010 it started passing support for Java back to Oracle.
A note on this page highlights the threats posed by the vulnerability discovered. As a workaround it recommends that you disable Java in browsers. The description reads as:
Starting with Java 7 Update 10, it is possible to disable Java content in web browsers through the Java control panel applet. Please see the Java documentation for more details.
Note: Due to what appears to potentially be a bug in the Java installer, the Java Control Panel applet may be missing on some Windows systems. In such cases, the Java Control Panel applet may be launched by finding and executing javacpl.exe manually. This file is likely to be found in C:\Program Files\Java\jre7\bin or C:\Program Files (x86)\Java\jre7\bin.
Also note that we have encountered situations where Java will crash if it has been disabled in the web browser as described above and then subsequently re-enabled. Reinstalling Java appears to correct this situation.
System administrators wishing to deploy Java 7 Update 10 or later with the “Enable Java content in the browser” feature disabled can invoke the Java installer with the WEB_JAVA=0 command-line option. More details are available in the Java documentation.
Every other day you get to see some report or the other screaming “Security update to address critical Java vulnerability released“ – as a result, many these days opt to uninstall Java completely – or at least disable it. This post on Staying safe on the Internet with Java; or being safer without it, is sure to interest you.
Leave a Reply