It’s not uncommon to see laptop manufacturers try to make an extra buck by preinstalling the system with malware and the best example for this was the Superfish debacle by Lenovo. This time around Dell seems to have done the same thing by preloading a self-signed root Certificate Authority with the name eDellRoot along with it came the private key which had explicitly marked it as non-exportable. The laptop buyer turned to Reddit after he confirmed with a pal of his whose answer was affirmative, when questioned about the existence of root certificate.
eDellRoot on Dell computers
This Certificate can snowball into a major controversy, as it has already been endangering the Dell customers who have bought the company’s machine in the recent past. However, it is yet to ascertain the batch of laptops coming with the root certificate, but it wouldn’t take much of skills to check it out either. The worst part of the entire controversy is that the root key has not come from any third party software’s, like in the case of Lenovo, but from Dells own Bloatware. This fact will prompt people to directly point fingers at Dell.
In case you have bought a new Dell machine and want to check if it is compromised by the certificate, here is what you can do.
Go to Start > Type “certmgr.msc”> Accept the UAC prompt > Trusted Root Certification Authorities > Certificates.
Now all you need to do is check if there is an entry named “eDellRoot”, if yes than you might be compromised as it is a self-signing certificate. If you see it on your laptop or desktop computer, you should remove it.
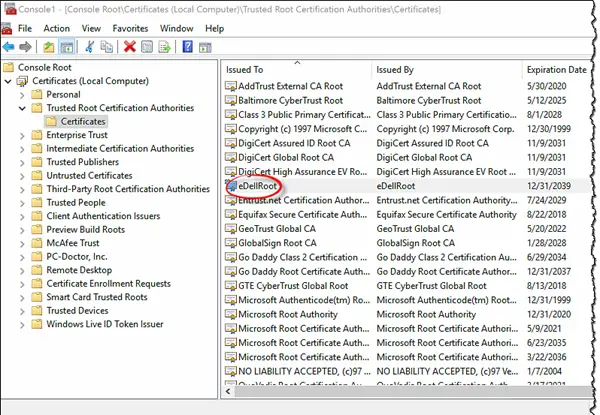
It is indeed surprising to see Dell do this even after the huge backlash Lenovo faced for its Superfish episode, the self-signed eDellRoot is a trusted root that expires only in 2039 and is marked as intended for “All” purposes, this makes it more powerful than the legit DigiCert certificate.
The properties of the certificate clearly outline that the user has a private key that corresponds to the root CA, which is definitely a bad news as the private key needs to be in the procession of certificate issuing computer.
Users of Internet Explorer, Edge, Chrome and other browsers which use the computer’s certificate store are affected. Users of Firefox are not affected as it has its own certificate store.
The Reddit user has also posted a link to the certificate, private key, and PFX file for the certificate.
UPDATE: Dell has posted an official response:
Today we became aware that a certificate (eDellRoot), installed by our Dell Foundation Services application on our PCs, unintentionally introduced a security vulnerability. The certificate was implemented as part of a support tool and intended to make it faster and easier for our customers to service their system. Customer security and privacy is a top concern and priority for Dell; we deeply regret that this has happened and are taking steps to address it. The certificate is not malware or adware. Rather, it was intended to provide the system service tag to Dell online support allowing us to quickly identify the computer model.
Some of you may want to try this free Root Certificate Scanner to scan Windows Root Certificates for untrusted one’s. Go here to see the eDellRoot certificate removal instructions.
You can also visit this site to see if it is installed on your Dell computer: https://edell.tlsfun.de/