CNBC website silently shared your passwords to third parties, according to reports. CNBC’s blog The Big Crunch, recently published an article “Apple and the construction of secure passwords,” offering tips on how to create a secure password.
CNBC shared your Password
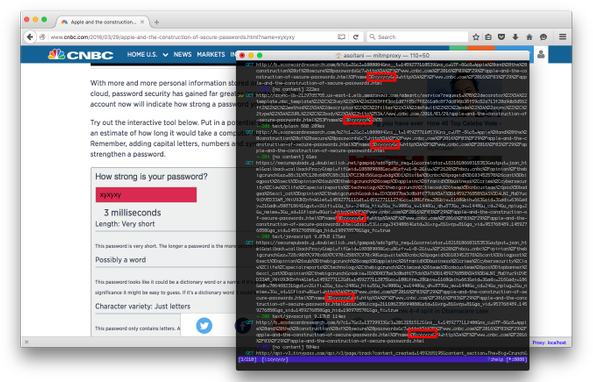
The article included a password checking tool to test the password strength. Thankfully, security expert Adrienne Porter Felt from the Google Chrome security team noticed that all passwords types in the form were unintentionally saved in a Google spreadsheet and were exposed to the third party marketers. Supposedly, the passwords were also stored in HTTP log files on the destination server.
Sophos reports,
“CNBC made things worse by sending unencrypted passwords to their server as a parameter in the page’s URL, which meant that anything else that the URL was shared with, such as 3rd party advertisers and web analytics providers, got a copy of the password being tested too”.
However, CNBC withdrew the article as soon as the issue was reported but it is still available in the cached form. Security firm Sophos stated that CNBC password tool saved the details on a non-secure, old and unencrypted HTTP connection making the hack-prone. Furthermore, your passwords were also added to the end of the reloaded URL of CNBC’s webpage.
Generally, the trusted password strength meters use the client-side code to test your password which runs in your browser and limits to your device. zxcvbn used by Dropbox and WordPress is one such password testing tool. As per the security norms, personal details like passwords should be sent over the secured and encrypted HTTP connection, but CNBC used server-side code thereby sending the passwords over the internet to a server leaving them open for marketers and hackers.
While CNBC tried to offer some genuine tips to get a strong password, but things went bad somehow.
You don’t mention that their website code was created by a company based in India. Hmm…
… Hmm. so you saw only the skin color?
No, just total stupidity from a specific set of people.
I think there is name for this attitude. Its called racialism.
Go back to munching your chips, you retard!