Internet users have been exposed to vulnerabilities in browser login managers for over 11 years. It has allowed your saved login data to be extracted by unscrupulous people, to be used for whatever they wish. It follows other revelations in the industry such as the Uber scandal that has allowed the personal data of users to fall into the wrong hands.
Your browser’s Password Manager may be leaking your user identity
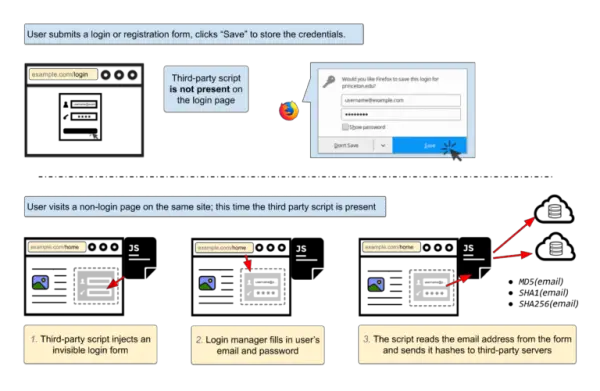
Technical site Freedom-to-tinker has helped expose the vulnerability to the general public that threatens to do untold damage to the industry. Yet again, users security has been compromised, and according to the report, the vulnerability has been known for many years.
So-called cross-site scripting (XSS) attacks could allow passwords to be stolen. But the main aim of these is user tracking by their email address. With the vulnerability being present for so many years, the question must be asked as to why it hasn’t been fixed? It seems that there is no straightforward answer and the silence from the industry has spoken volumes.
It appears that the issue is from the framework in which login managers are designed. Freedom-To-Tinker has suggested that the industry needs to work with a new framework that enhances security for end users. They insist that site managers could be doing more to prevent this potential data loss and that the number of sites that are affected is startling.
Users are asked to be vigilant and not store their passwords in browser login managers. It is really down to the large browser companies such as Google, Mozilla, and Microsoft to close these vulnerabilities, but until they do, you should treat your password with great care. While the responsibility arguably doesn’t rest with you, it will be you who will have to deal with the aftermath, and you need to be increasingly careful online.
You can test the attack yourself on this demo page. Please check more details here.
Leave a Reply