The latest news reports suggest that the BACP or British Association for Counseling & Psychotherapy website has been hit by a variant of the CTB-Locker ransomware. The variant of ransomware,from the family of CTB-Locker, is actually the first ever ransomware family created to target websites, and not computers.
Ransomware hijacks a website
BACP is a professional body representing counseling and psychotherapy with qualified and experienced members that works toward a better standard of therapeutic practice. Following the attack, the attackers now hold the website to a ransom.
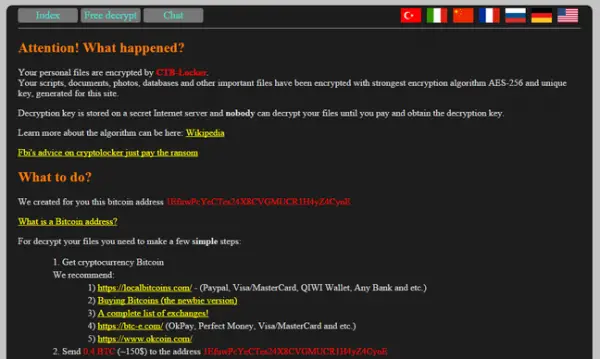
The greeting page of the website now bears a message outlining instructions on how to pay off the extortionists: An amount of $150 (£100) in Bitcoin must be credited into the account mentioned by February 22, failing which the association’s web data will remain scrambled forever.
“Your scripts, documents, photos, databases and other important files have been encrypted with strongest encryption algorithm AES-256 and unique key, generated for this site. Decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the decryption key”, reads the front page of the hijacked website.
How the ransomware functions
The ransomware, CTB-Locker, encrypts files on infected machines, and then demands payment for the decryption key. Without this key, the contents are likely to lose its value. So far, it is believed the ransom has not been paid as the crooks’ Bitcoin wallet appears to be empty and no currency has been moved from it.
What’s worth mentioning here is that CTB-Locker is known to affect Windows computers in general and BACP.co.uk appears to be powered by Linux, probably kernel version 2.6.32 to 2.6.35. The ransomware generally gets installed when a user inadvertently opens a spam email attachment or browsing a malicious website.
I think that they should track down these idiots down and physically rough them up. This would send a message that this type of extortion will not be tolerated, ever. It seems like governments don’t give a care about this type of activity, it takes too long for them to respond (bureaucratic red tape), and they allow these criminals get away with it.
To make sure my browser does not get compromised, I use a portable version of Firefox (with a backup) and if my browser gets compromised, I can simply replace the hijacked web browser with the backup version. Use CCleaner to continually clear your cache and configure your browser to delete the cache on exit. Also, continually clear your /TEMP folders to get rid of unwanted junk files. Also, create manual restore points on your Windows 10 machine so you can reset it back to the last good restore point.
Also, stay away browser from Microsoft, (IE and Edge); they are the primary targets for these boneheads.
Knowing that recently some (e.g., TOR-based) ransomware is coded in cross-platform nw.js, I’m interested in following this to see if ransomware can actually now run on Linux despite certain runtime dependencies found in Windows but not Linux (theory: if someone engineers it someone can reverse-engineer or block). But as Malwaretips and other observe, though BACP site runs on Fedora if this truly were CTB-Locker it’d rename server’s index.html/index.php file so it couldn’t load a homepage (which checking just now from USA BACP is loading homepage)…maybe just Linux.Encoder with ability to generate HTML ransom/defacement pages? Thanks for reminding security community evil minds are definitely now after ANY OS which could yield them a penny, so keep eyes open; cheers!