Microsoft has shared few important tips to folks who are into network security, administration and design. Microsoft has shared details on aspects like having a right defender mindset, security dependencies and effectively designing and managing graphs.
Defender Mindset
In the instances of network compromises everything turns out to be like a battlefield and it all depends on how defenders fight the battle against network adversaries.
The approach taken by defenders is to focus on protecting their assets, prioritizing them, and sorting them out by workload and business function. Defenders are covered in lists of assets—in system management services, in asset inventory databases, in BCDR spreadsheets.
In reality, defenders do not have a list of assets—they have a graph. Assets are connected to each other by security relationships in the form of graph. Attackers try to breach a network by landing somewhere in the graph using techniques like spearphishing, from where they start the process of hacking by finding vulnerable systems by navigating the graph.
Security Dependencies
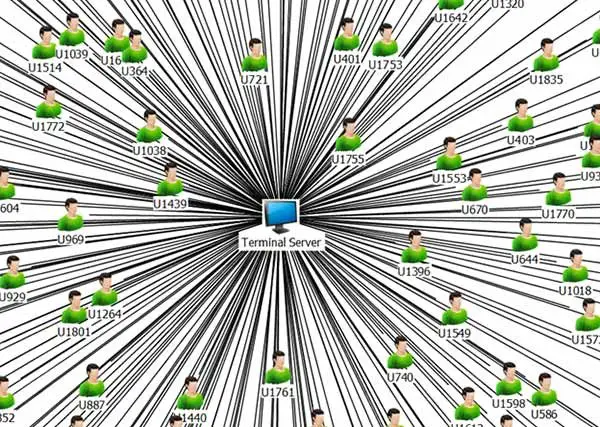
In the case of Windows network, whenever the users want to perform certain kinds of logons using Interactive, Terminal Server, and others – the entered users’ credentials are exposed to potential theft if the underlying host is already compromised. There are other kinds of relationships that causes security dependencies:
- In a set up where all local administrator accounts have a common password – compromise the first system and dump the local admin password, use this password on other hosts with the same password.
- File servers which hosts the logon scripts that run for many users and software update servers.
- Print servers which deliver print drivers to client machines.
- Certificate authorities that issue certificates valid for smart card logons.
- Database admins that can run code under the context of a database server running as a privileged user.
A machine that has a vulnerability can also be compromised, suddenly allowing attackers to create new edges in the graph. Or users may have an account in two untrusted domains with the same password, which creates a hidden edge between these domains.
How should Defenders combat Attackers?
As a defender, you can always combat the attackers by effectively managing the graph and by visualising the network by transforming your lists into graphs and then by implementing the following controls to prune the graph:
- Thoroughly examine the unwanted edges that leads to huge connectivity bursts. Also, implement infrastructure partitioning and credential silos to reduce these unwanted edges.
- Reduce the number of administrators. Also make use of Just-In-Time / Just Enough techniques for privilege minimization.
- Two-factor authentication technique can help mitigate certain edge traversals.
- In case, if a user account is compromised, apply a solid credential rotation approach.
- Rethink forest trust relationships.
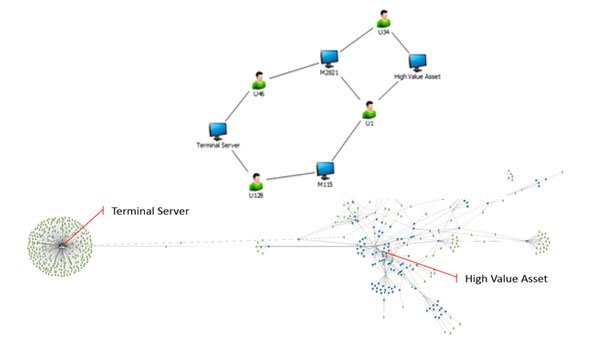
Defenders need to make sure that attackers do not have a leg up on them when visualizing the battlefield. Following this approach, defenders can have an upper hand as they would be having full information about their own network, whereas attackers need to study the network, part by part, says Microsoft.
Defenders should learn from the attackers on how they understand the graph – Attackers study the infrastructure as it is and not as an inaccurate mental model, viewed from an incomplete asset inventory system, or a dated network diagram. One should prepare with a Defenders Mindset to face the reality.
Leave a Reply