Discovering a malicious attacker on your network is not only worrisome but quite dangerous. If that’s less, imagine having 6 of them, all on the same network! It’s a story of cyberespionage that Microsoft’s Detection and Response Action Team (DART) uncovered very recently.
Microsoft’s DART uncovers real-life cybercrime stories
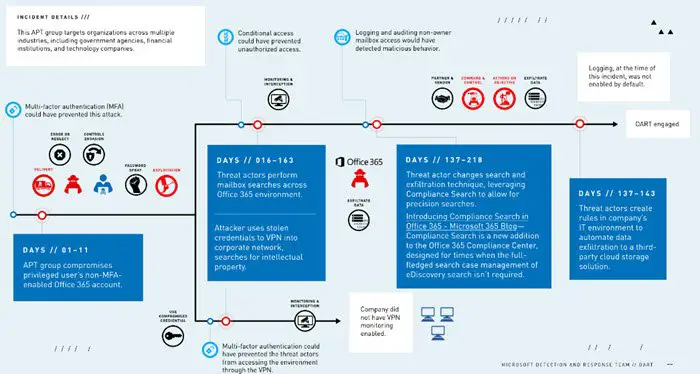
An APT had infiltrated a multi-national company’s networks after stealing administrator credentials. It then gained access to sensitive emails by using sophisticated techniques. Despite multiple attempts, the company failed to remove the malicious actor. As a result, the threat remained in the network for 240 days. To reverse this occurrence, Microsoft DART was brought onsite to help the company gain back control and investigate.
Upon thorough investigation, DART found there were five additional threats. Responding to compromises, the team conducted investigations and identified certain targeted mailbox searches and compromised accounts, as well as attacker command-and-control channels.
This investigation lasted greater than seven months and revealed a attainable compromise of delicate data – pertaining to the sufferer and the sufferer’s clients – saved in Workplace 365 mailboxes. 243 days after the preliminary compromise, DART was then introduced in to work alongside the incident-response vendor and the corporate’s in-house groups, said Microsoft in a report.
Following an investigation, a comprehensive assessment of all Microsoft operating systems in the organization was conducted to ensure no other APT actors were present. Also, a robust plan was initiated to regain control of the customer’s environment, secure its assets against future intrusion, and enable monitoring and detection in the event of future attempts to compromise the company’s network.
Learning from the incident, Microsoft outlined five basic steps that organizations can deploy to reduce their exposure to APT attackers, including enabling MFA. These include,
- Removing legacy authentication
- Adequately training first responders
- Properly logging events with a security
- Information and event management product
- Acknowledging the facts that attackers do use legitimate administrative and security tools to probe targets.
For more information, check this MSSecurity PDF.
Leave a Reply