In an effort to aid security researchers to understand cyberattacks that leverage Artificial intelligence and the latest tools, Microsoft has released an open-source cyberattack simulator called as CyberBattleSim. With CyberBattleSim, researchers can create simulated network environments, see how they fare against AI-controlled cyber agents, and assess their current security weaknesses.
Cybersecurity remains the top agenda with attacks being carried out every now and then. Recently, the University of California issued a warning to its students and staff of a ransomware group having stolen and published their personal data and that of hundreds of other schools, government agencies, and companies nationwide.
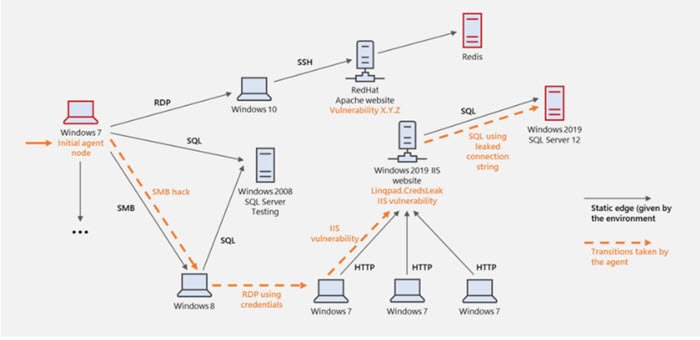
How CyberBattleSim works
CyberBattleSim is based on Open AI Gym, an open platform for artificial intelligence training. During a cyberattack when the attacker attempts to take over some part of the network exploiting inherent vulnerabilities, CyberBattleSim simulates the vectors of the distribution of malicious code within the network, helping defenders monitor the attack.
CyberBattleSim builds a highly abstract simulation of the complexity of computer systems, making it possible to manufacture cybersecurity challenges in the context of reinforcement learning. During the attack simulation, defenders and researchers manually create various nodes on the network listing what services are running, what vulnerabilities are already present, and what security controls are in place. Automated agents, that represent threat actors, are deployed in the attack simulation to randomly execute actions as they try to take over the nodes.
Further, as the attackers attempts to gain control over the network, the defender agent can monitor network activity to detect the attacker’s presence and prevent the attack.
Vulnerability Outcomes
CyberBattleSim provides vulnerability outcomes such as,
- leaked user or network credentials
- leaked references to other computer nodes,
- leaked node properties
Some examples of Remote vulnerabilities include :
- SharePoint site exposing ssh credentials
- an ssh vulnerability that grants access to the machine
- a GitHub project leaking credentials in the commit history
- SharePoint site with a file containing SAS token to the storage account
While local vulnerabilities may include:
- Extracting authentication token or credentials from a system cache
- Escalating to administrator privileges
CyberBattleSim is Microsoft’s initiative to leverage machine learning and AI to continuously improve security and automate more work for defenders. A recent study done by the company reveals that three-quarters of organizations say their teams spend too much time on tasks that should be automated. With this tool Microsoft wants researchers to explore how autonomous systems and reinforcement learning can be harnessed to build resilient real-world threat detection technologies and robust cyber-defense strategies.
The open-source Python source code is available here.
Next read – Best Cybersecurity Practices for Small Business