As researchers predict, ‘Ransomware as a service’ market will continue to flourish in 2020. Of course, Ransomware attacks have become highly advanced over the period of time – with attackers actively targeting hospitals, hotels, businesses, and whatnot! However, in order to neutralize the ransomware threat, experts need to be one step ahead of cybercriminals in figuring out the pattern they follow with respect to different metrics.
27% of ransomware attacks occur on weekends
Researchers at FireEye have identified a number of common characteristics in initial infection vectors, dwell time and after-hours ransomware deployment. Researchers accumulated the data from several ransomware incidents of the past. Researchers also uncovered a link between these attacks and financially motivated groups like FIN6, TEMP.MixMaster, etc.
The majority of these ransomware attacks were carried out by a variety of means. For example, Remote Desktop Protocol (RDP) or other remote access, Phishing with malicious link or attachment, and drive-by download were among the common intrusion techniques.
“Post-compromise and interactive ransomware deployment increased in 2018 and 2019. This allows attackers to identify key systems to maximize the effectiveness of end-stage operations.”
In most cases, attackers obtained access to the victim’s computer using the Remote Desktop Protocol (RDP). In other cases, attackers were also caught brute-forcing the credentials. Phishing campaigns like Trickbot and Emotet also cause the initial intrusion.
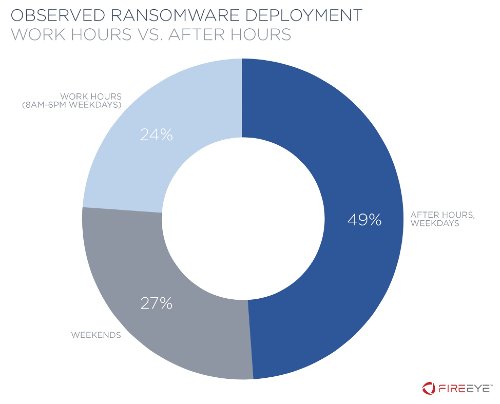
As per the findings, cybercriminals take at least 3 days to launch a full-fledged ransomware attack after causing the initial infection. Interestingly, researchers also uncovered that in 76 percent of incidents, ransomware was executed outside work hours.
Researchers have discovered that 49% of malware execution occurred after work hours on weekdays, followed by 27% on weekends, and 24% during work hours on weekdays.
Ransomware operators apparently increase urgency and the probability of payment with the help of a strategy. Attackers also tend to increase the price after the stipulated time and in some cases, offer the option to decrypt a portion of the impacted machine for a lower price.
Meanwhile, here’s how you can safeguard yourself from human-operated ransomware attacks.
Leave a Reply