A new malware that targets Linux-based Internet of Things (IoT) devices has been detected by Search-Lab, a Security research and development firm. This Linux ARM malware called as ELF_IMEIJ.A exploits a vulnerability in devices from AVTech, a surveillance technology company.
ELF_IMEIJ.A has drawn attention from Trend Micro who says that it is similar to the deadly Mirai and attacks defenseless IoT devices, in this case, cameras, CCTV equipment, and network recorders that support the AVTech cloud.
Linux operating systems which have been the preferred by Internet of Things (IoT) manufacturers continue to see focused security threats owing to their higher deployment in smart systems across many different industries. ELF_IMEIJ.A joins a group of recently discovered Linux malware that exploits the ARM platform on Linux devices. ARM is widely used for IoT and mobile devices, making it a necessary hurdle for attackers targeting these devices.
Linux malware ELF_IMEIJ.A can initiate DDoS attacks
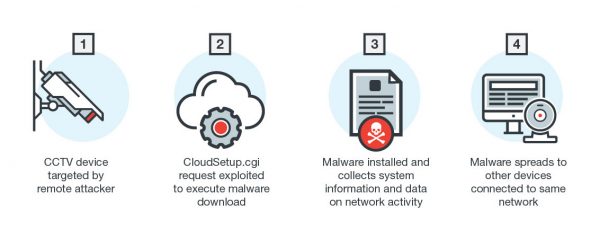
ELF_IMEIJ.A arrives via RFIs in cgi-bin scripts. A remote attacker sends a request to random IP addresses and attempts to take advantage of the vulnerability.
Specifically, it exploits CloudSetup.cgi, the reported AVTech CGI Directory vulnerability, to execute a command injection that triggers the malware download. The attacker tricks the device into downloading the malicious file and changes the file’s permissions to execute it locally.
Once this Linux malware is installed onto the device, it gathers system information and network activity data. It can also execute shell commands from the malicious actor, initiate Distributed Denial of Service (DDoS) attacks, and terminate itself. Infected devices also put other devices connected to the same network at risk.
There are three IP addresses where ELF_IMEIJ.A can be downloaded, and they are hosted on two separate ISPs.
- hxxp://172.247.116.3:8080/Arm1
- hxxp://172.247.116.21:85/Arm1
- hxxp://192.154.108.2:8080/Arm1
What happens to AVtech users
AVTech has over 130,000 different devices connected to the Internet, so this attack may be used to gain and maintain persistent access to these devices. The devices can also be turned into bots and used to drive large-scale DDoS attacks. Like most connected devices, the targets are not secured by default and are impossible to monitor directly.
Search-Lab disclosed the vulnerability to AVTech on October 2016 but did not get any response. Since then, there have been several attempts to contact, but AV-Tech has failed to respond.
As an AVTech user, you can do the following to protect your device,
- Change the default admin password
- Never expose the web interface of any Avtech device to the internet
Visit Search-Lab & TrendLabs to learn more about this.
Leave a Reply