Petya…NotPetya… now Not a Ransomware! Reports from leading security researchers suggest NotPetya, an infection that invaded computers worldwide is a Wiper (since it overwrites parts that a disk needs to run) and not a Ransomware. An analysis of the encryption routine of the malware used in the Petya/ExPetr attacks revealed that designers of the malware did not design it as a ransomware for financial gain but as a wiper pretending to be ransomware.
The NotPetya attack was not financially motivated, but was used as a cyper webon to cause destruction say security researchers.
NotPetya Malware is a Wiper
In the light of above statement, it can be safely assumed that the companies and agencies hit by this cyberattack might never be able to recover their data. Regions that were hard hit by NotPetya included Ukraine, Asia, Russia, the US, parts of Europe and Australia.
How to find if your system is infected with NotPetya
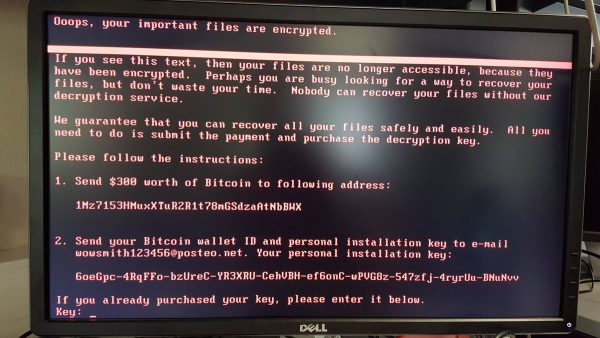
The file-scrambling software targets mainly Microsoft Windows PCs on a corporate network. Once infected, the malware tries to pass infection from one system to another. Basically, it uses a build of open-source Mimikatz that has been tweaked to extract network administrator. Besides, it also uses a modified version of leaked EternalBlue SMB exploit, used by WannaCry. When infected, the systems display a plain black background with red text.
Although, designers of the campaign demands $300 in Bitcoin to unscramble the hostage data, the mechanisms put in place for money collection from victims in exchange for decryption keys raise serious doubts as it disintegrates quickly.
The malware has been named as NotPetya since it differs from its variant – Petya in a way that it just doesn’t encrypt files, but also overwrites and encrypts the master boot record (MBR). For more information, read this post.
Leave a Reply