Ransomware groups show little to literally zero respect to critical industries including healthcare, especially when the entire world is fighting against the on-going crisis. As a lot of businesses have transitioned to working remotely, critical industries continue to endure challenges. At a time when the world is fighting a pandemic, ransomware groups continue to leverage the current situation to their advantage.
Microsoft describes how Ransomware groups continue to target healthcare, critical services. They’ve also outlined a strategy on how to mitigate the overall risk factor.
Ransomware continues to target healthcare & other critical services
In its recent blog post, Microsoft wrote:
“At a time when remote work is becoming universal and the strain on SecOps, especially in healthcare and critical industries, has never been higher, ransomware actors are unrelenting, continuing their normal operations.”
In the first two weeks of April, Microsoft observed an uptick in the number of ransomware deployments. Microsoft says multiple ransomware groups activated at least dozens of ransomware deployments targeting the healthcare industry this month.
These attackers largely affected aid organizations, medical billing companies, manufacturing, transport, government institutions, and educational software providers. One thing is certain. These attacks are not limited to critical services since major IT firms like Cognizant are also falling prey to ransomware attacks.
According to Microsoft security intelligence as well as the company’s Detection and Response Team (DART) team, this is clearly not the first of these attacks that have surfaced.
“Many of the compromises that enabled these attacks occurred earlier.”
Microsoft sees a pattern that is more or less similar to human-operated ransomware campaigns. Attackers have been targeting networks target networks for several months beginning earlier this year while the ransomware deployments happen to be part of their monetization strategies.
Most of these attacks start with the lateral movement technique when attackers try to exploit vulnerabilities in network devices and remote desktop servers exposed to the Internet. As a result, attackers use brute force to compromise RDP servers in large numbers.
“The attacks delivered a wide range of payloads, but they all used the same techniques observed in human-operated ransomware campaigns.”
RDP or Virtual Desktop endpoints without multi-factor authentication are susceptible to ransomware attackers. Plus, Older platforms no longer getting security updates, and Misconfigured web servers also remain subject to ransomware related risks.
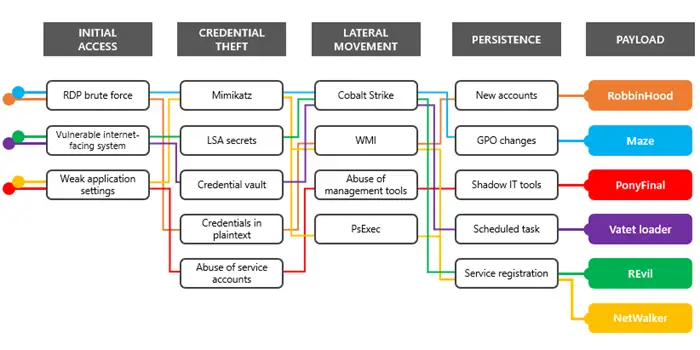
Microsoft warns users against some of the deadliest ransomware families such as:
- RobbinHood ransomware,
- Vatet loader,
- NetWalker ransomware,
- PonyFinal ransomware,
- Maze ransomware,
- REvil ransomware, etc.
Microsoft is already working to protect Hospitals against ransomware attacks, however.
Leave a Reply