One of the leading cyber intelligence firm, the iSight Partners, today announced a zero-day vulnerability which is impacting several widely used software. Further, the report revealed that Russian hackers have exploited this bug in all supported versions of Windows Server 2008 & Windows Server 2012 and Microsoft’s Windows Operating System.
How iSight came across the exploitation of this bug in Russia
The company discovered the misuse of a zero-day vulnerability during a cyber-espionage campaign which attributed Russia. During the course of this campaign in 2009, iSight realized the occurrence of various illegal activities in order to gain access to the confidential information. But, the Russian hackers started using this bug in the late summer and certainly gained some access to their targets.
The company quoted:
The use of this zero-day vulnerability virtually guarantees that all of those entities targeted fell victim to some degree.
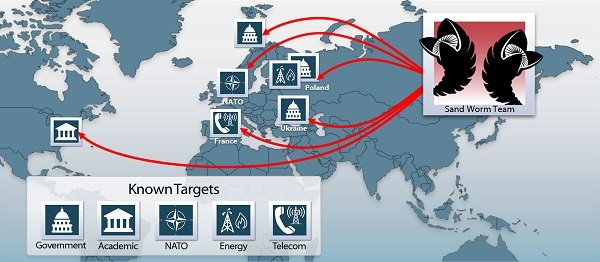
iSight has named these recent Russian hackers as the Sandworm Team because these hackers used the encoded references to the sci-fi “Dune” series in their attacks.
Visible Targets of the Hackers
The domains at potential threat include:
- NATO
- Western European Government Organization
- Ukrainian Government Organization
- Energy Sector Firms (especially Poland)
- European Telecommunication Companies
- United States Academic Organization
The report noted that:
iSIGHT Partners has been monitoring the Sandworm Team’s activities from late 2013 and throughout 2014 – the genesis of this team appears to be around 2009. The team prefers the use of spear-phishing with malicious document attachments to target victims. Many of the lures observed have been specific to the Ukrainian conflict with Russia and to broader geopolitical issues related to Russia. The team has recently used multiple exploit methods to trap its targets including the use of BlackEnergy crimeware, exploitation of as many as two known vulnerabilities simultaneously, and this newly observed Microsoft Windows zero-day.
How attackers used this bug
The researchers at iSight believe that the so-called spear-phishing techniques are involved in the exploitation of this zero-day vulnerability. The hackers sent an infected Power Point documents to their targets, which when opened, probably allowed these attackers to gain control of the victim’s computer by remotely executing the arbitrary codes.
Microsoft is expected to release an update today as a part of the patch Tuesday to fix this potential vulnerability.
Leave a Reply