The sole activity undertaken by data researchers, reverse engineers, and security professionals to provide the first line of defense against any security threats is data collection. It helps in manual data analysis through multiple repetitive operations which help in developing effective solution systems. TrendMicro, a global leader in providing enterprise data security and cyber security solutions has created a flexible toolkit to aid this process – DefPloreX.
DefPloreX, A Machine-Learning Toolkit
The tool is based on open-source libraries for efficiently analyzing millions of defaced web pages. It can also be used on web pages planted as a result of an attack in general.
DefPloreX (a play on words from “Defacement eXplorer”) uses a combination of machine-learning and visualization techniques to turn unstructured data into meaningful high-level descriptions Real-time information on incidents, breaches, attacks, and vulnerabilities are efficiently processed and condensed into browsable objects that are suitable for efficient large-scale e-crime forensics and investigations, mentions TrendMicro Blog.
How TrendMicro DefPloreX works?
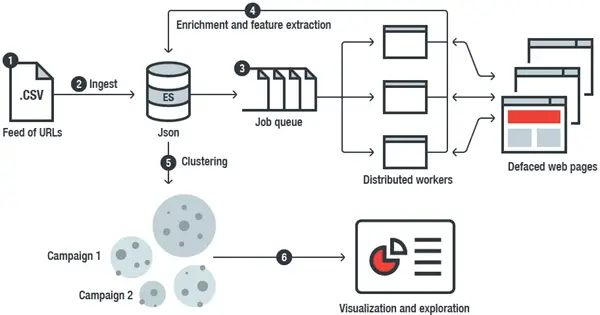
The ingenious tool ingests plain and flat tabular files (e.g., CSV files) containing URLs. It then proceeds to explore their resources with headless browsers, extracts features from the deface web pages, and stores the resulting data to an Elastic index. Then, using a multitude of Python-based data-analysis techniques and tools, DefPloreX creates offline “views” of the data, allowing easy pivoting and exploration. It also runs a feature called “Data bucketing,” which most of us use to derive a compact representation of each record. This compact representation is then used to enable fast clustering.
Finally, a good feature about DefPlorex is that the tool keeps the amount of memory used in all its operations to the bare minimum without compromising the performance. Moreover, it works well on a simple laptop and can readily be scaled up when more computing resources are available in the loop.
For more information, visit TrendMicro Blog.
Leave a Reply